How to Secure Business Communication Channels from Cyberattacks

Modern organizations increasingly depend on digital communication channels as foundational operational infrastructure, not just productivity tools. Email, enterprise messaging, voice and video calls, and file-sharing platforms now underpin day-to-day collaboration, leadership coordination, decision-making, and the execution of critical business and public-sector functions.
As workforces become more distributed and collaboration increasingly cloud-based, the volume and sensitivity of information exchanged through communication channels continues to grow. Operational data, financial details, personal information, strategic plans, and regulatory documentation routinely move through messaging systems and virtual meetings. As a result, business communication infrastructure has become a core component of an organization’s digital ecosystem.
At the same time, the security model surrounding communication has not always evolved at the same pace as usage. Many organizations rely on a mix of legacy email systems, consumer-grade messaging apps, and third-party collaboration platforms that were not designed with enterprise security, privacy, or regulatory compliance as foundational principles. This creates uneven protection, fragmented governance, and increased exposure to risk.
Common attack vectors include phishing emails, compromised messaging applications, man-in-the-middle attacks, and unauthorized data interception, all of which can expose organizations to financial loss, operational disruption, regulatory penalties, and long-term reputational damage. According to the Verizon Data Breach Investigations Report, phishing and credential theft remain among the leading causes of data breaches worldwide.
Securing business communication channels is therefore no longer limited to protecting individual messages or user accounts. It requires a comprehensive approach that addresses identity, encryption, access control, device security, governance, and human behavior.
Why Business Communication Channels Are a Prime Target for Cyberattacks
Business communication channels have become a preferred target for cybercriminals because they concentrate human trust, sensitive data, and organizational authority into a single, highly accessible layer of the digital environment.
Unlike traditional infrastructure attacks that target servers or networks directly, communication-based attacks exploit legitimate systems and trusted user behavior. Email platforms, messaging applications, and collaboration tools are inherently designed to enable rapid interaction and information sharing, making them ideal vehicles for deception, impersonation, and covert data access.
These channels routinely carry high-value information, including authentication details, financial transactions, internal operational data, legal communications, intellectual property, and discussions between leadership teams. When attackers gain access to communication platforms, they often bypass multiple layers of technical defense, gaining visibility into internal processes without triggering conventional security alerts.
Another factor contributing to increased risk is the blurring of internal and external communication boundaries. Modern communication platforms are used not only within organizations but also with partners, suppliers, contractors, and external stakeholders. This expanded ecosystem increases exposure and creates additional opportunities for attackers to exploit weak links, compromised accounts, or insufficient access controls.
In many cases, communication platforms also generate extensive metadata—information about who is communicating, when, and how often—which can be just as valuable to attackers as message content itself. Poorly governed communication environments can unintentionally expose this metadata, increasing the risk of surveillance, profiling, or regulatory non-compliance.
As a result, business communication channels have evolved into a high-impact attack surface. When compromised, they can be used to initiate fraud, manipulate decision-making, distribute malware, or serve as a launch point for broader system intrusion. This makes communication security a critical component of any comprehensive cybersecurity and risk management strategy.
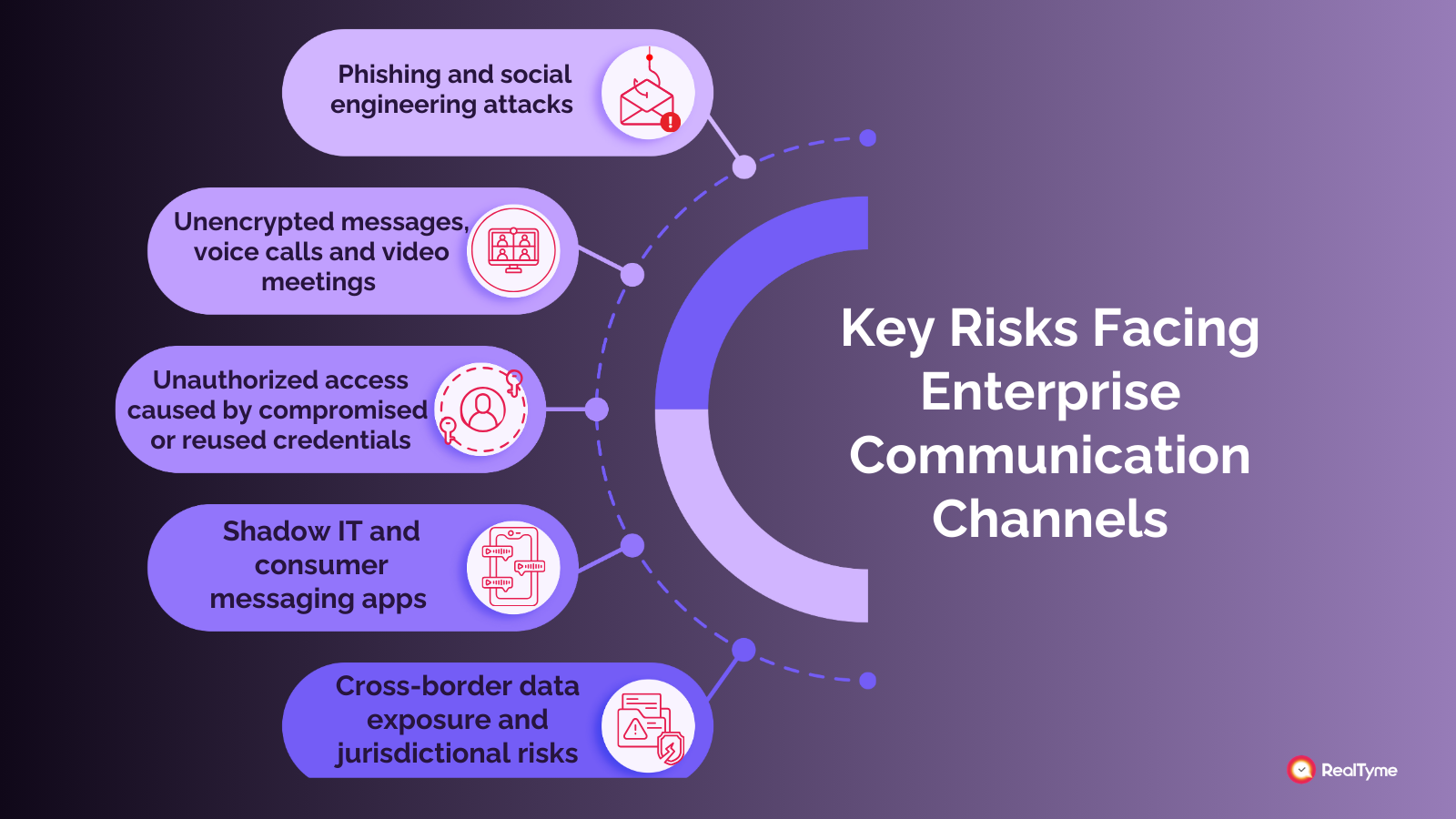
Key Risks Facing Enterprise Communication Channels
Modern enterprises face a wide range of communication-related cybersecurity risks, including:
- Phishing and social engineering attacks that exploit trust and impersonate executives, partners, or internal teams.
- Unencrypted messages, voice calls, and video meetings that can be intercepted or monitored by unauthorized parties.
- Unauthorized access caused by compromised or reused credentials, often obtained through credential-stuffing or malware.
- Shadow IT and consumer messaging apps used without IT oversight, creating blind spots in security and compliance.
- Cross-border data exposure and jurisdictional risks, where messages and metadata are stored or processed outside approved regions.
Because communication tools are designed for speed and ease of use, security controls are often overlooked or misconfigured. This makes them an ideal entry point for attackers looking to move laterally within a network, escalate privileges, or exfiltrate sensitive data.
The Hidden Cost of Insecure Communication
Without appropriate security safeguards, business communication channels can quickly become the weakest link in an organization’s overall security posture. A single compromised email, message, call, or shared file can provide attackers with access to sensitive information or trusted workflows, often without triggering immediate detection. Because communication platforms are designed to facilitate speed and collaboration, they are frequently exploited through phishing, impersonation, and credential-based attacks that rely on deception rather than technical sophistication.
The financial impact of communication-related security incidents is substantial. Attacks originating from email and messaging platforms are commonly associated with fraud, ransomware, and business disruption. Beyond direct financial losses, organizations must account for the cost of incident response, forensic investigations, system recovery, legal counsel, and long-term remediation efforts. In large enterprises and public-sector environments, even a single incident can result in significant unplanned expenditure and prolonged operational impact.
The consequences extend well beyond financial loss. Insecure communication channels introduce serious regulatory and compliance risks, particularly when platforms are used to exchange personally identifiable information (PII), confidential records, or regulated data. A breach may trigger mandatory disclosure obligations, regulatory investigations, audits, and potential fines under frameworks such as GDPR or sector-specific regulations. For organizations operating across multiple jurisdictions, inconsistent data protection and data residency controls in communication platforms can further increase exposure.
Reputational damage is often the most enduring and difficult cost to recover from. When internal or external communications are exposed, manipulated, or misused, trust is eroded among customers, partners, employees, and public stakeholders. This loss of confidence can lead to reduced engagement, strained partnerships, increased regulatory scrutiny, and long-term damage to organizational credibility.
1. Choose Secure, Enterprise-Grade Communication Platforms
Not all communication tools are built with enterprise security requirements in mind. Many widely used consumer messaging and collaboration platforms prioritize speed and convenience over security, privacy, and compliance. As a result, organizations often have limited visibility into how data is stored, who can access it, and where that data is processed or retained.
To reduce cyber risk and protect sensitive business information, organizations should adopt enterprise-grade secure communication platforms specifically designed for professional and regulated environments. These platforms provide stronger security controls, centralized governance, and compliance-ready features that consumer tools typically lack.
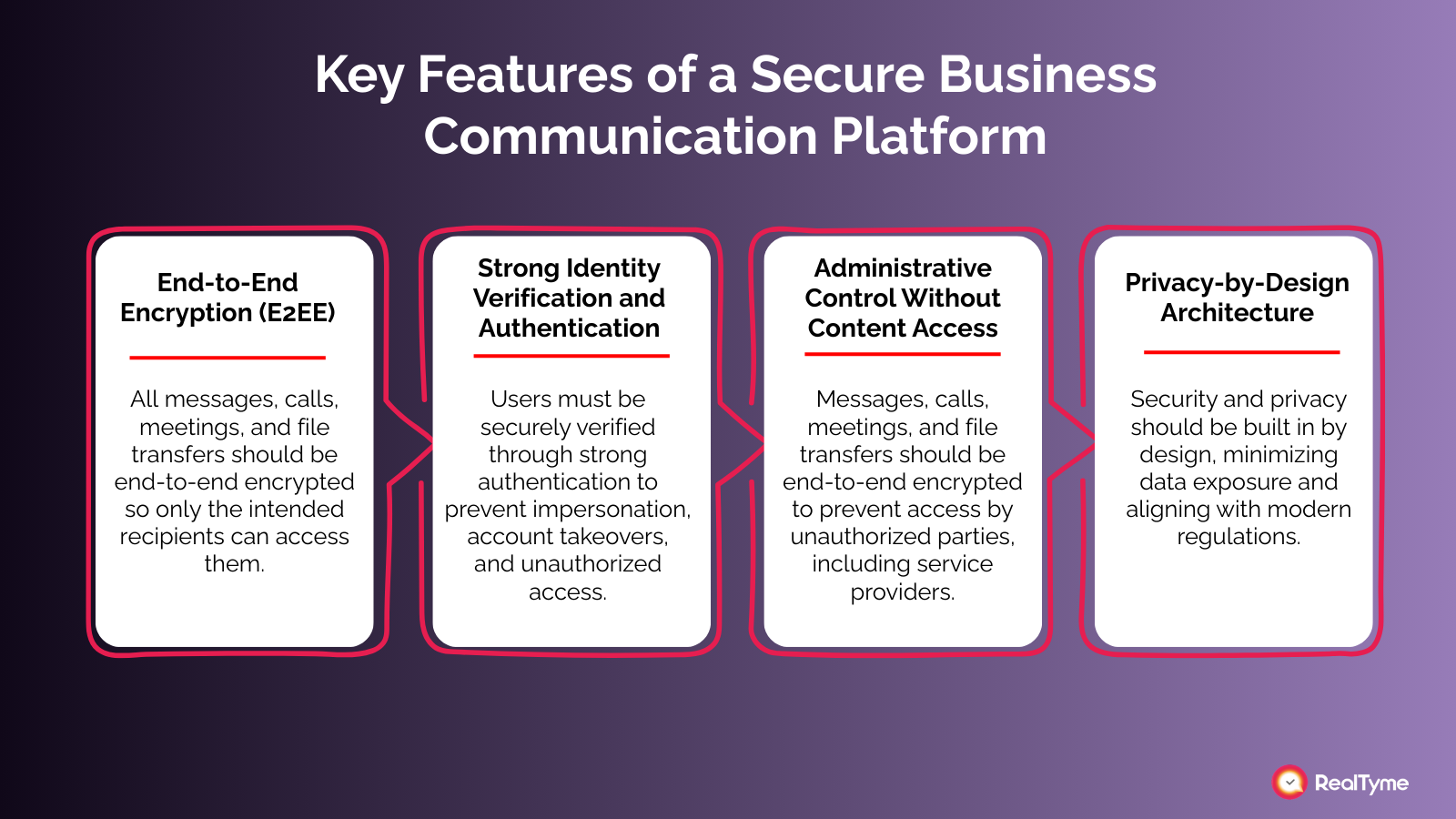
Key Features of a Secure Business Communication Platform
When evaluating secure communication solutions for enterprises, organizations should look for the following essential capabilities:
- End-to-End Encryption (E2EE)
Messages, voice calls, video meetings, and file transfers should be encrypted from sender to recipient. End-to-end encryption ensures that data cannot be intercepted, read, or accessed by unauthorized parties, including service providers.
- Strong Identity Verification and Authentication
Users must be securely verified through robust authentication mechanisms. This reduces the risk of impersonation, account takeover, and unauthorized access caused by stolen or compromised credentials.
- Administrative Control Without Content Access
IT and security teams should be able to manage users, enforce policies, and monitor compliance without having access to message content. This separation supports privacy, trust, and regulatory compliance while maintaining operational control.
- Privacy-by-Design Architecture
Security and privacy should be embedded into the platform’s architecture from the outset, not added as an afterthought. A privacy-by-design approach minimizes data exposure, limits metadata collection, and aligns with modern data protection regulations.
By choosing secure, enterprise-grade communication platforms, organizations can significantly reduce their attack surface, strengthen data protection, and ensure confidential communication across teams, partners, and borders. This foundational step is critical for building a resilient and compliant business communication strategy in today’s evolving threat landscape.
2. Enforce Strong Authentication and Access Controls
Passwords alone are no longer sufficient to protect modern business communication channels. Stolen, weak, or reused credentials remain one of the leading causes of data breaches and unauthorized access, especially across email, messaging, and collaboration platforms.
To strengthen security and reduce the risk of account compromise, organizations must implement robust authentication and access control mechanisms across all communication channels.

Access Control and Authentication Best Practices
A secure enterprise communication strategy should include the following best practices:
- Multi-Factor Authentication (MFA)
MFA adds an additional verification layer beyond passwords, such as biometrics, hardware tokens, or one-time codes. This significantly reduces the risk of unauthorized access, even if credentials are compromised.
- Role-Based Access Control (RBAC)
RBAC ensures users can only access communication channels, conversations, and data necessary for their specific role. Limiting privileges minimizes the potential impact of insider threats and lateral movement by attackers.
- Context-Aware and Zero Trust Principles
A Zero Trust approach assumes no user or device should be trusted by default. Every access request must be continuously verified based on identity, device posture, and context, reducing the risk of persistent or hidden threats.
By enforcing strong authentication and granular access controls, organizations can dramatically reduce their attack surface, prevent unauthorized access, and strengthen the overall security of their business communication environment.
3. Encrypt Business Communication in Transit and at Rest
Encryption is a foundational pillar of secure business communication. Without strong encryption in place, intercepted messages, voice calls, video conferences, and shared files can be read, modified, or exploited by cybercriminals. For organizations handling sensitive or regulated data, encryption is a critical security requirement.
To protect communication data throughout its entire lifecycle, organizations must ensure encryption is applied both in transit and at rest across all communication channels.
Encryption Best Practices for Secure Business Communication
A comprehensive encryption strategy should include the following best practices:
- Default Encryption for All Communication Channels
All messages, voice calls, video meetings, and file transfers should be encrypted by default, without requiring user action. This ensures consistent protection and eliminates human error.
- Secure Transport Protocols
Industry-standard protocols such as Transport Layer Security (TLS) should be used to protect data as it travels across networks, preventing eavesdropping and man-in-the-middle attacks.
- Strong Key Management Practices
Encryption keys must be securely generated, stored, rotated, and protected from unauthorized access. Poor key management can undermine even the strongest encryption algorithms.
- End-to-End Encryption for Sensitive Use Cases
End-to-end encryption ensures that only the intended sender and recipient can access communication content, preventing third parties; including service providers—from viewing or intercepting data.
End-to-end encryption is especially critical for high-risk and regulated environments such as government, financial services, energy, and critical infrastructure. In these sectors, secure encrypted communication is essential for maintaining confidentiality, meeting regulatory requirements, and protecting national and organizational security.
4. Secure Devices and Networks Used for Business Communication
Even the most secure communication platform can be compromised if the devices and networks used to access it are not properly protected. Endpoints such as laptops, smartphones, and tablets—as well as corporate and remote networks—are frequent targets for attackers seeking to intercept or manipulate business communications.
To ensure end-to-end communication security, organizations must protect the entire environment in which communication tools operate.
Device and Network Security Essentials
A strong device and network security strategy should include the following measures:
- Mobile Device Management (MDM)
Implement MDM solutions to enforce device encryption, strong screen locks, secure configurations, and remote wipe capabilities for corporate and approved personal devices used for work.
- Secure Remote Access
Employees accessing communication tools remotely should use encrypted connections, such as VPNs or secure access gateways, to prevent data interception over public or untrusted networks.
- Regular Updates and Patch Management
Operating systems, communication applications, and supporting software must be kept up to date. Timely patching closes known vulnerabilities that attackers commonly exploit.
Securing business communication requires a holistic approach that extends beyond the application itself to the devices, networks, and access points employees rely on every day.
5. Reduce Human Risk Through Security Awareness and Clear Policies
Human error remains one of the leading causes of cybersecurity incidents affecting business communication channels. Phishing emails, malicious links, impersonation attempts, and social engineering attacks often exploit trust, urgency, and lack of awareness rather than technical weaknesses.
Reducing human risk requires continuous education and clear organizational policies.
Building a Security-Aware Communication Culture
Organizations should take the following steps to strengthen their human defense layer:
- Train Employees to Recognize Threats
Regular training should help employees identify phishing attempts, suspicious messages, fake links, and unusual requests across email and messaging platforms.
- Establish Clear Communication Policies
Define which communication tools are approved for business use and specify how sensitive information should be shared and stored.
- Limit Use of Consumer Messaging Apps
Consumer-grade messaging applications often lack enterprise security controls and compliance features, increasing the risk of data leakage and shadow IT.
- Promote Shared Responsibility for Security and Privacy
Encourage a culture where employees understand their role in protecting sensitive information and feel empowered to report potential threats.
With clear guidance and ongoing awareness, employees become a strong line of defense rather than a security vulnerability.
6. Monitor, Audit, and Prepare for Communication Security Incidents
Securing business communication channels is an ongoing process—not a one-time implementation. Threats evolve, usage patterns change, and new vulnerabilities emerge over time.
To maintain a strong security posture, organizations should implement continuous oversight and preparedness measures.
Monitoring and Incident Readiness for Communication Systems
Best practices include:
- Continuous Monitoring for Suspicious Activity
Monitor communication systems for unusual behavior, unauthorized access attempts, or abnormal usage patterns that may indicate a breach.
- Regular Security Audits and Risk Assessments
Conduct periodic audits to evaluate the effectiveness of communication security controls and identify gaps or emerging risks.
- Clear Incident Response Procedures for Communication Breaches
Maintain and regularly test an incident response plan specifically addressing communication-related security breaches, ensuring rapid containment and recovery.
Early detection and rapid response can significantly reduce the impact of a cyberattack, limit data exposure, and protect business continuity.
Secure Communication Is About Trust
At its core, secure business communication is about trust; trust between employees, leadership teams, partners, customers, and public institutions. In an era of constant cyber threats, every message, call, and shared file must be protected to preserve confidentiality, integrity, and confidence in day-to-day operations.
By combining secure communication platforms, strong authentication and access controls, end-to-end encryption, user awareness, and privacy-by-design principles, organizations can safeguard their most critical conversations and operate securely in an increasingly complex and hostile digital environment.
RealTyme was built to meet this exact need; delivering secure, compliant, and sovereign communication for organizations that cannot afford compromise. Designed for highly sensitive and regulated environments, RealTyme ensures that trust is not assumed, but embedded into every interaction.
To see how secure, privacy-first communication works in practice, contact the RealTyme team or request a free trial of the RealTyme platform.



