Secure Communication Strategies for Cybersecurity Teams

At 2:17 a.m., the incident response channel lights up.
A production system is offline. Unusual outbound traffic has been detected from a database server. A security engineer joins the war room, followed by the on-call incident commander, infrastructure leads, and eventually the CISO. Logs begin streaming in. Screens fill with telemetry. The first containment steps are debated.
No one realizes that the attacker has been present in the organization’s collaboration platform for nearly two weeks.
They are not just inside the network. They are inside the conversation.
As credentials are reset and containment plans are drafted, the attacker quietly watches. They see which systems defenders believe are affected. They observe how quickly the team moves. They learn which backups are trusted, which environments are prioritized, and which accounts hold administrative access. Every decision becomes intelligence.
By morning, the breach has expanded.
Scenarios like this are real. Over the past several years, multiple high-profile incidents have demonstrated that attackers increasingly target internal communication systems. In several widely reported breaches, attackers maintained access to internal collaboration systems for days or weeks, using them to observe incident response in real time. In some cases they monitor chat channels to understand response plans. In others, they impersonate trusted users to influence decisions. Sometimes they simply remain silent observers, using internal coordination as a real-time intelligence feed.
For modern cybersecurity teams, communication is a critical component of the attack surface.
This risk is especially acute in industries where internal conversations themselves are highly sensitive. Government agencies, defense organizations, financial institutions, healthcare providers, and companies handling intellectual property or regulated data often exchange information that would be damaging if exposed in real time. In these environments, internal coordination during an incident may include classified data, customer financial records, national security considerations, or confidential business strategy. For these sectors, secure communication is a matter of regulatory compliance, contractual obligation, and, in some cases, national security.
This article explores how security leaders and engineers can design, secure, and operationalize communication systems that remain trustworthy even when parts of the environment are compromised.
Communication as an Intelligence Layer for Attackers
Secure incident communication refers to the ability of cybersecurity teams to coordinate response, share sensitive operational information, and make decisions through communication channels that remain confidential, authenticated, and resilient during an active cyberattack. A secure incident communication platform is therefore a core component of modern security architecture, particularly for CISOs, government agencies, and organizations operating in regulated or high-risk environments.
Security teams exchange some of the most sensitive information in an organization through communication tools. Incident response plans, architectural context, access procedures, and leadership decisions all flow through chat platforms, email, video calls, and ticketing systems. These conversations often reveal far more strategic insight than any single compromised server ever could.
For organizations operating in regulated or high-risk sectors, this exposure has direct business consequences. A compromised communication channel during an incident can lead to delayed containment, regulatory reporting failures, market impact, or loss of public trust. Boards and executive teams increasingly expect CISOs to ensure that incident coordination itself remains secure, auditable, and resilient. As a result, communication security is becoming a board-level concern, particularly for enterprises handling confidential customer data, government contracts, or critical infrastructure.
Attackers understand this. Modern intrusions frequently involve identity compromise rather than purely technical exploitation. Once an attacker controls a trusted account or session, they may gain access to collaboration platforms that provide a continuous stream of defender activity. Even if encryption is strong, a compromised endpoint or hijacked session can provide visibility into messages as they are written and read.
This visibility changes the nature of an incident. Instead of reacting blindly, an attacker can adapt in real time. They can delay actions until containment steps are announced, move laterally based on observed priorities, or manipulate the response by impersonating team members. The result is not just a technical breach, but an informational advantage.
For CISOs and security engineers, this reality requires a shift in mindset. Communication environments must now be architected as part of the security perimeter itself.
Understanding the Threat Model
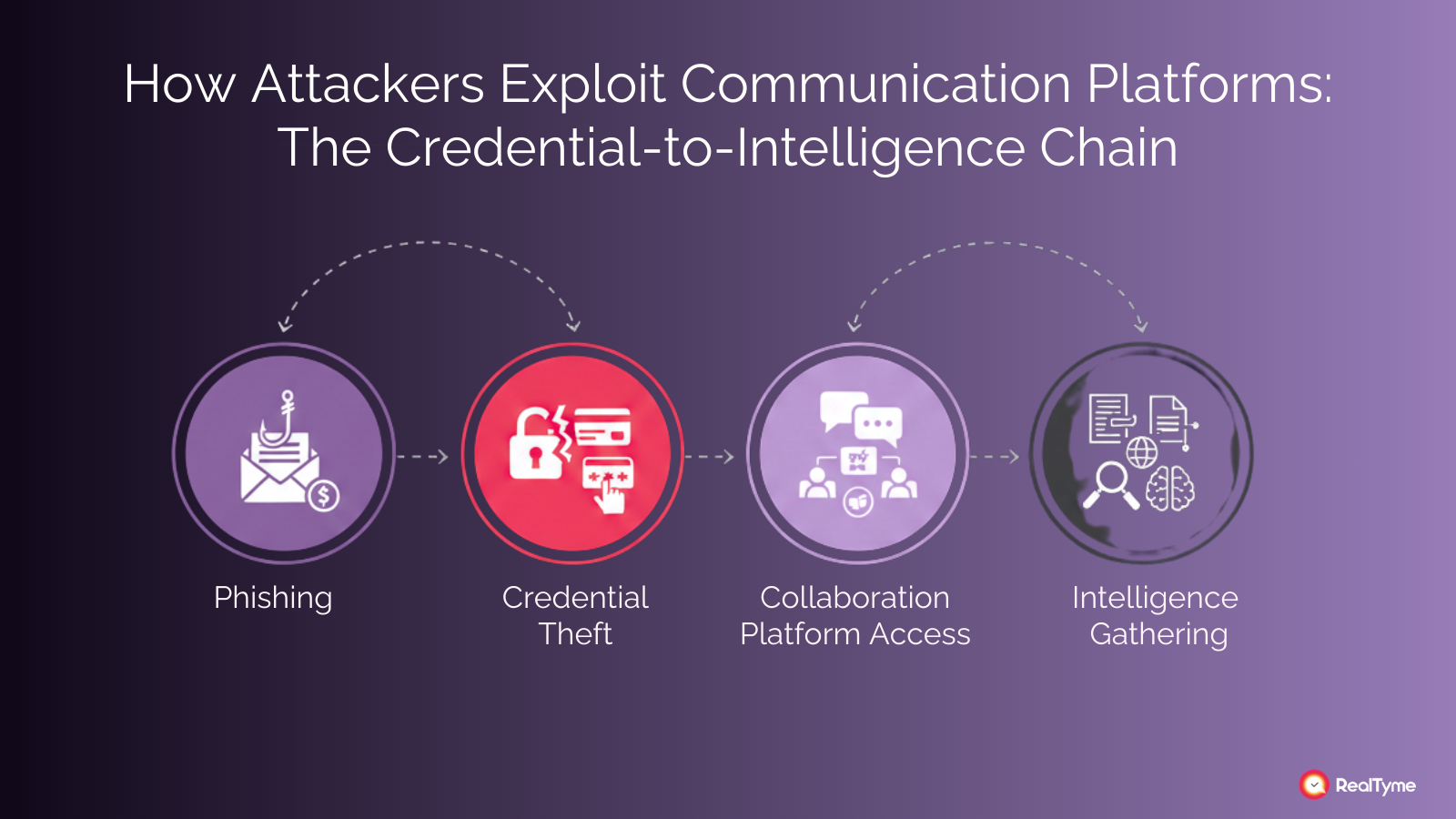
Designing secure communication begins with understanding how these systems are typically compromised. Rarely does an attacker break encryption directly. Instead, they exploit identity, session control, or endpoint visibility. A phishing attack may capture credentials or tokens that provide persistent access to collaboration tools. Malware on a developer’s workstation may capture screen content or browser sessions. A compromised contractor account may quietly join internal channels. Administrative export features in SaaS platforms can sometimes be abused to extract message histories.
In each case, the attacker does not need to disrupt communication to benefit from it. Simply observing can be enough. Watching an incident response unfold provides context about infrastructure, dependencies, and internal processes that might otherwise take weeks of reconnaissance to gather.
In government and critical-infrastructure environments, the stakes are even higher. Attackers targeting public institutions, utilities, or defense contractors often seek strategic visibility rather than immediate disruption. Monitoring internal coordination allows them to understand response timelines, interagency communication, and decision-making hierarchies. This type of intelligence can be used not only to prolong an intrusion but also to influence geopolitical or economic outcomes. For organizations operatingin these sectors, secure internal communication is an essential component of operational resilience.
A mature communication security strategy assumes that partial compromise is always possible. The goal is not to eliminate all risks but to ensure that even if an attacker gains visibility into one channel or account, they cannot immediately exploit the information to accelerate damage.
Treating Communication Systems as Tier-Zero Security Infrastructure
Many organizations invest heavily in endpoint protection, network segmentation, and cloud security while leaving collaboration platforms governed primarily by IT policies. This separation no longer reflects reality. Communication systems should be classified alongside identity providers and privileged access systems as tier-zero assets.
This classification changes how they are monitored and controlled. Authentication events from collaboration platforms should feed into the same detection pipelines as VPN and cloud logins. Unusual access patterns, new device registrations, or suspicious exports of message history should trigger investigation. Third-party integrations and OAuth permissions deserve the same scrutiny as any external application connecting to production systems.
As security leaders formally recognize communication platforms as critical infrastructure, they allocate the monitoring, access control, and incident response planning required to protect them. Increasingly, that includes introducing dedicated secure coordination environments for incident response and high-sensitivity operations. Secure communication platforms such as RealTyme are built with this use case in mind, providing controlled, secure communication spaces that operate alongside existing collaboration tools while offering stronger guarantees around access control, confidentiality, and operational integrity during critical events.
Encryption, Visibility, and Trust
Encryption remains a foundational control for secure communication, but its role must be understood clearly. Many enterprise tools encrypt messages in transit and at rest, yet still allow administrative access or provider-level visibility under certain conditions. Even with strong encryption, compromised endpoints or hijacked sessions can expose message content.
For everyday operations, enterprise-grade encryption combined with strong identity controls may be sufficient. However, during high-severity incidents, organizations often benefit from stronger guarantees. Some security teams maintain dedicated secure communication environments for incident response that offer tighter access control, shorter retention, and limited integrations. Others rely on ephemeral channels that reduce the amount of historical data available to a potential attacker.
The objective is not to eliminate collaboration but to ensure that the most sensitive discussions occur in environments designed for confidentiality and integrity under pressure.
In environments where incident communication may involve regulated data, government coordination, or highly confidential intellectual property, purpose-built secure communication platforms can provide additional assurance. RealTyme, for example, enables organizations to create isolated, encrypted coordination environments for high-severity incidents, helping ensure that sensitive discussions remain protected even if other collaboration systems are under investigation or partially compromised.
Segmentation and the Principle of Least Exposure
A common weakness in communication architecture is the tendency to centralize everything into a single environment. Routine operational discussions, incident response coordination, executive decision-making, and long-term strategy often coexist in the same channels. This convenience creates unnecessary exposure. If a single account or session is compromised, an attacker may gain insight into far more than intended.
Segmentation provides resilience. Separating day-to-day operational communication from high-severity incident channels limits the amount of information visible through any single compromise. Restricting executive crisis communication to smaller, tightly controlled environments reduces the risk of impersonation or manipulation. Applying shorter retention policies to incident channels ensures that sensitive details do not persist indefinitely.
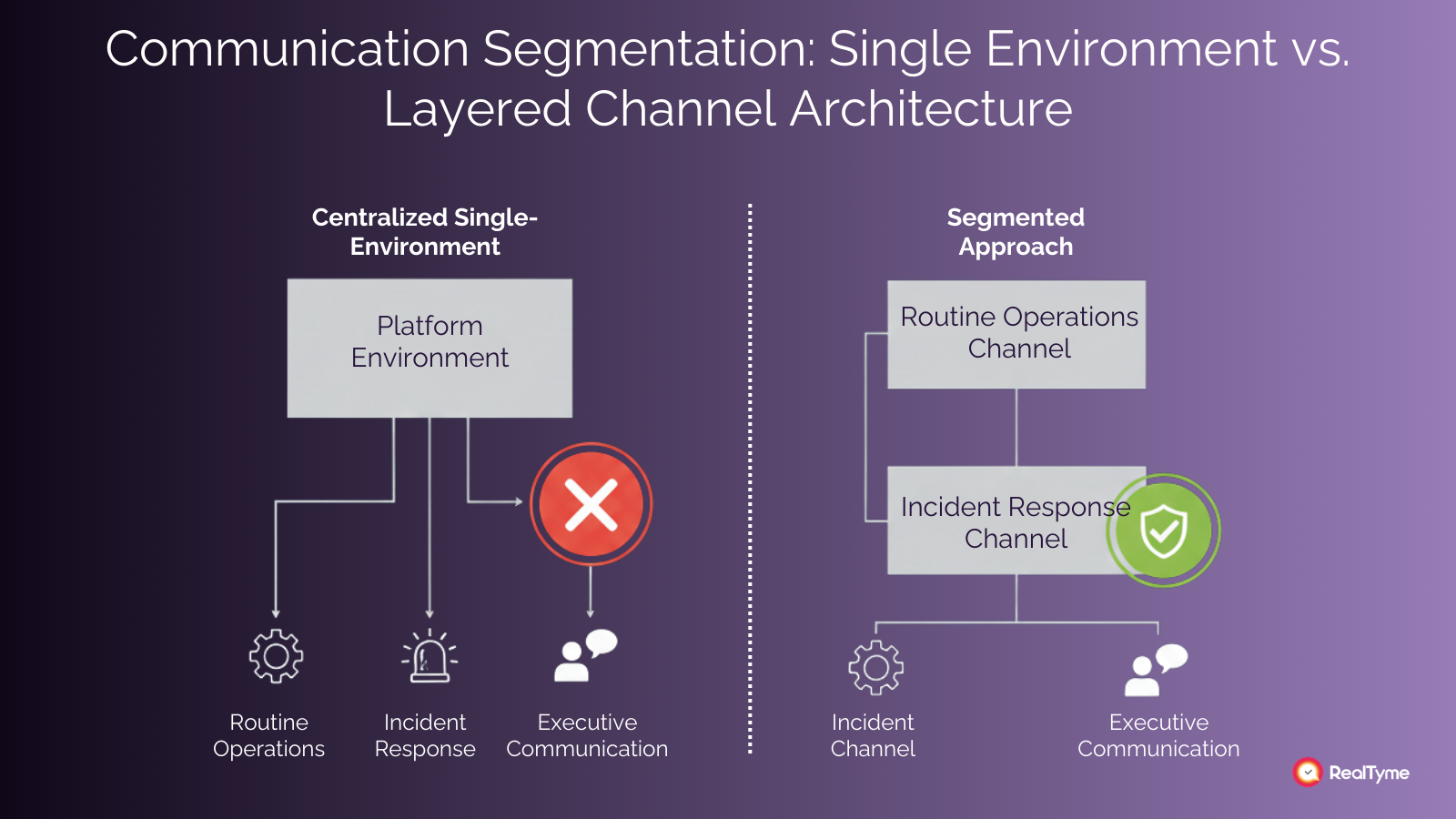
Some organizations go further by maintaining separate environments or dedicated “war room” platforms that are activated only during significant incidents. This approach reduces the blast radius if routine collaboration tools are compromised.
Zero Trust for Communication
Zero Trust principles are often applied to networks and cloud access, but they are equally relevant to communication. Security teams should operate under the assumption that any account or device could be compromised. This does not mean abandoning collaboration; it means designing processes that remain secure even when trust is uncertain.
Sensitive credentials and recovery codes should never be transmitted through chat or email. Instead, teams can share references or access paths to secure vaults. High-risk requests, such as privileged account changes or infrastructure shutdowns, should be verified through independent channels. Pre-established identity verification procedures can help confirm that a message truly originates from the expected person.
By designing communication workflows that assume potential compromise, organizations ensure that attackers cannot immediately leverage observed conversations.
Identity as the Core Security Control
In most real-world incidents involving collaboration platforms, the root cause is identity compromise. Once an attacker controls a trusted account, they can read messages, impersonate users, and influence decisions. Strong identity security thereforebecomes the foundation of secure communication.
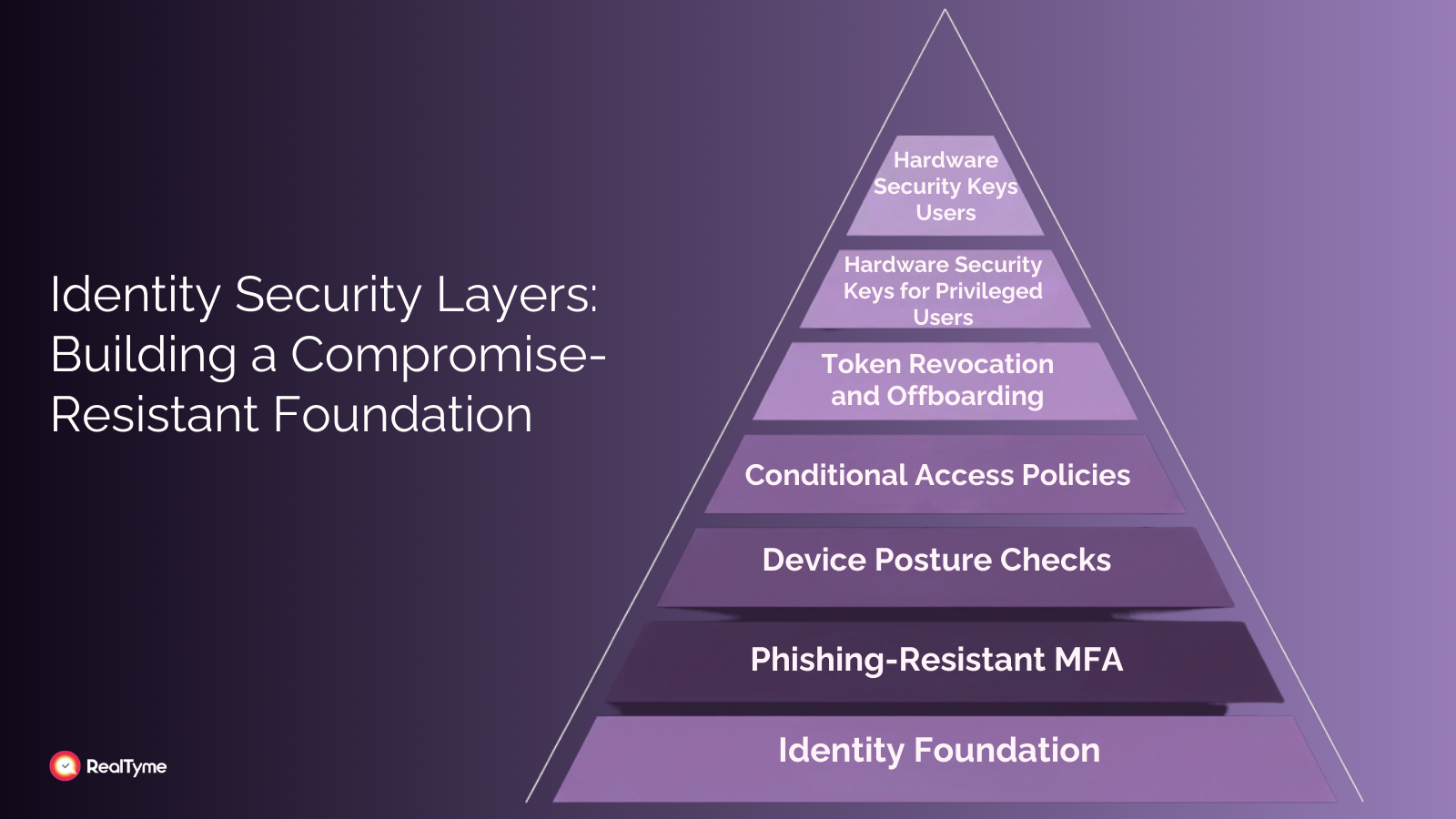
Phishing-resistant multi-factor authentication, device posture checks, and conditional access policies significantly reduce the risk of unauthorized access. Rapid token revocation and automated offboarding processes prevent lingering access after roles change. For privileged users and incident commanders, separate administrative identities and hardware security keys add an additional layer of protection.
Protecting identity is not just about preventing unauthorized logins. It is about preserving the integrity of decision-making during high-pressure situations.
Monitoring Communication Platforms Like Production Systems
Because collaboration tools are central to operations, they should be monitored with the same rigor as production infrastructure. Authentication anomalies, unusual geographic access, rapid channel membership changes, or unexpected message exports can all indicate compromise. Integrating collaboration platform logs into the broader security monitoring environment allows SOC teams to detect and respond to these signals quickly.
Monitoring also provides valuable context during an investigation. Understanding who accessed which channels and when can help determine whether an attacker gained visibility into response activities.
Managing Retention and Historical Risk
Long message histories provide convenience and context, but they also create risk. Years of archived conversations may contain detailed discussions of architecture, vulnerabilities, and past incidents. If an attacker gains access to these archives, they gain a strategic map of the organization.
A thoughtful retention strategy balances operational needs with risk reduction. Sensitive incident channels may benefit from shorter retention periods. Access to message exports and search capabilities should be tightly controlled and audited. Encryption of archives and backups protects against unauthorized access at rest.
Reducing the volume of historical data does not eliminate risk, but it limits the amount of intelligence available to a potential adversary.
Social Engineering Inside Trusted Channels
Security awareness programs often focus on email phishing, but attackers increasingly exploit internal communication channels. A compromised account can be used to send urgent messages requesting access changes or to share malicious links that appear legitimate. In high-stress situations, teams may act quickly without verifying the source.
Training should emphasize that internal messages are not automatically trustworthy. Unusual or high-risk requests should always be confirmed through independent channels. Some organizations now run simulations that mimic compromised chat accounts to help teams practice verification procedures.
Building and Rehearsing a Communication Playbook
When a serious incident occurs, confusion and urgency can undermine even well-designed systems. A documented communication playbook provides clarity. It defines which platforms are used for different severity levels, who is authorized to communicate externally, how identity is verified, and when to transition to backup channels.
Equally important is rehearsal. Tabletop exercises that simulate tool compromise or identity compromise help teams practice operating under uncertainty. These exercises reveal gaps in process and build confidence that communication can remain secure even during chaotic events.
Incident Communication Playbook: Core Elements
1. Platform by severity level — Document which tool is used at each tier. Example: Tool for routine ops, your secure incident environment for severity-1 and severity-2 events, a phone bridge or out-of-band channel if the primary platform is suspected compromised.
2. Participant authorization rules — List who is auto-included in an incident channel, who requires explicit approval to join, and which external parties (legal, PR, vendors) are excluded by default until a named decision-maker approves their access.
3. Identity verification protocol — Any in-channel request involving credential resets, privileged access changes, or system shutdowns must be confirmed via a separate channel before action is taken. Define what that second channel is in advance.
4. External communication gates — Name the specific roles authorized to communicate with regulators, customers, and press. All others default to silence until cleared.
5. Suspected channel compromise trigger — Define the signals that should prompt the team to assume the communication channel itself is compromised (e.g., unexpected participants, unusual message behavior, alerts from your monitoring pipeline) and specify the exact fallback sequence.
6. Retention and documentation policy — State upfront that the incident channel has a defined retention window and will not serve as the record of the incident. Point participants to where the authoritative incident log lives.
Rehearsing these elements through tabletop exercises ensures teams can execute under pressure without improvising.
Designing a Secure Incident Communication and War Room Environment
Many organizations are rethinking how they coordinate during major incidents. Instead of relying solely on general-purpose collaboration tools, they are adopting environments designed specifically for high-trust coordination. These environments emphasize restricted membership, strong authentication, limited integrations, and short retention periods.
Unlike general-purpose collaboration tools, secure incident communication platforms such as RealTyme are designed specifically for high-sensitivity coordination, controlled access, and resilience during active cybersecurity incidents.
Platforms purpose-built for secure incident communication and coordination — including solutions like RealTyme — are increasingly being adopted by enterprises, government agencies, and critical-infrastructure operators that require a trusted environment for high-stakes collaboration. By providing dedicated incident war rooms with tightly controlled access and strong security guarantees, these platforms help ensure that response coordination remains confidential and reliable even when broader collaboration environments may be under scrutiny or partially compromised.
The goal is not to replace existing tools but to provide a resilient layer for the moments when security matters most.
Balancing Security and Usability
Security controls that are too restrictive can drive teams to use unauthorized tools or personal devices. Effective communication security must therefore balance protection with usability. Tools should be secure by default, fast during incidents, and intuitive under pressure. When secure options are easier to use than insecure ones, teams naturally adopt them.
Secure Communication in Regulated and High-Risk Industries
Organizations operating in regulated or high-risk environments face unique communication challenges. Financial institutions must protect discussions involving market-moving information and customer data. Healthcare providers must coordinate incidents involving protected health information. Government agencies and defense contractors may handle classified or sensitive operational details. Technology companies and research organizations must protect intellectual property and strategic planning.
In these sectors, communication during an incident is not merely operational. It is often subject to regulatory scrutiny, legal discovery, and contractual obligations. Ensuring that coordination remains confidential and auditable is essential not only for effective response but also for compliance and trust. Dedicated secure communication environments, such as RealTyme, are increasingly being adopted to support these requirements while enabling teams to move quickly and decisively.
Conclusion: Protecting the Conversations That Defend the Organization
Cybersecurity programs have long focused on protecting systems and data. Today, they must also protect coordination and decision-making. Communication platforms are now a primary attack surface because they reveal how defenders respond. When attackers gain visibility into those conversations, they gain a powerful advantage.
Organizations that treat communication as critical infrastructure, apply Zero Trust principles, and design secure incident coordination environments will be better prepared to respond effectively. By ensuring that conversations remain confidential, authentic, and resilient, they protect not only their systems but their ability to defend them.
As organizations mature their incident response capabilities, many are incorporating dedicated secure coordination platforms like RealTyme into their security architecture to ensure that sensitive conversations remain protected when they matter most.
In modern cybersecurity operations, secure communication is no longer a supporting function. It is a core defensive capability. How a team communicates during a crisis directly shapes how effectively it can defend.
Frequently Asked Questions About Secure Incident Communication
Why is secure communication important during a cyber incident?
Because attackers often monitor internal channels to understand response strategies, secure communication ensures that containment plans and sensitive decisions remain confidential.
What is a secure incident communication platform?
A secure incident communication platform is a system designed specifically for cybersecurity coordination, offering strong access control, encryption, auditability, and resilience during high-risk events.
Who needs secure communication tools?
CISOs, SOC teams, incident responders, government agencies, critical infrastructure operators, and enterprises handling sensitive or regulated data.
How is RealTyme different from standard collaboration tools?
RealTyme is purpose-built for high-trust coordination during security incidents, providing controlled communication environments designed to remain secure even when parts of the broader IT environment may be compromised.
This article was written by the RealTyme security team, who work with enterprises, government agencies, and critical infrastructure organizations to improve secure incident coordination and operational resilience.


