Why WhatsApp Isn’t Enough for Sovereign Government Communication

Security without sovereignty is not security at all, especially when national interests and sensitive data are at stake.
Over the past decade, WhatsApp has become synonymous with fast, reliable, and encrypted communication. Its clean interface and global adoption have made it a favored tool not just for personal use, but increasingly for unofficial professional communication including within government ranks.
Ministers, diplomats, civil servants, and security officials have gravitated toward WhatsApp because it works, it’s familiar, and it’s instant.
However, beneath the surface of its convenience lies a serious and escalating problem. While WhatsApp offers end-to-end encryption, it does not offer the sovereignty, transparency, or control required for sensitive government communication.
For governments, the stakes are significantly higher. Protecting national interests, citizen data, intelligence operations, and diplomatic channels requires far more than encryption. It requires complete ownership of data, infrastructure, and encryption keys — none of which WhatsApp provides.
Real-World Example: The Spanish Prime Minister Hack
A dramatic illustration of this risk occurred in 2022, when Pegasus spyware was used to compromise the mobile phone of Spanish Prime Minister Pedro Sánchez. Attackers exploited a vulnerability in a consumer-grade messaging application to gain deep access to his device. Once inside, they extracted sensitive files, communication logs, and location data, all while circumventing official communication channels and controls.
This incident highlights a disturbing truth: even encrypted platforms like WhatsApp are vulnerable, and when governments rely on them, they expose themselves to foreign surveillance, unauthorized data access, and national security breaches.
WhatsApp’s Security Features vs. Sovereign Requirements
To understand WhatsApp’s appeal, we must acknowledge what it does well:
- End-to-End Encryption: WhatsApp uses the Signal Protocol to encrypt messages in transit, which means only the sender and receiver can read the contents.
- Two-Factor Authentication (2FA): Adds a basic layer of identity verification to protect user accounts.
- Widespread Familiarity: It’s already installed on millions of government officials’ phones, making it a default choice in urgent situations.
Yet these features, while suitable for individuals, fall apart when applied to the requirements of a sovereign nation.
WhatsApp’s Limitations in the Government Context
1. Data Residency Concerns
Government messages and backups are stored on Meta-owned infrastructure, often outside the country’s jurisdiction. This means a foreign corporation controls the infrastructure through which sensitive national communications are routed. Moreover, data on Meta servers is not encrypted at rest, exposing it to internal data mining and access under U.S. law.
2. No Sovereign Key Ownership
WhatsApp manages and stores encryption keys on its own systems. Governments cannot control or audit the cryptographic infrastructure. In a scenario where national policy, intelligence, or legal interests are at stake, this lack of sovereign control is unacceptable.
3. Limited Administrative Controls
WhatsApp was never designed for organizational oversight. It lacks role-based access, usage policies, compliance integrations, or the ability to revoke access centrally. Governments have no visibility into how data is used, shared, or stored beyond the app interface.
4. Metadata Exposure
WhatsApp collects extensive metadata, including contact graphs, timestamps, geolocation, device data, and usage behavior. Even if messages are encrypted, this metadata can reveal operational patterns, internal networks, and strategic movements.
5. No Service-Level Agreement (SLA)
WhatsApp does not offer any guarantees around uptime, support, or compliance alignment. Updates are rolled out without notice, creating unpredictable security risks and breaking points for government institutions.
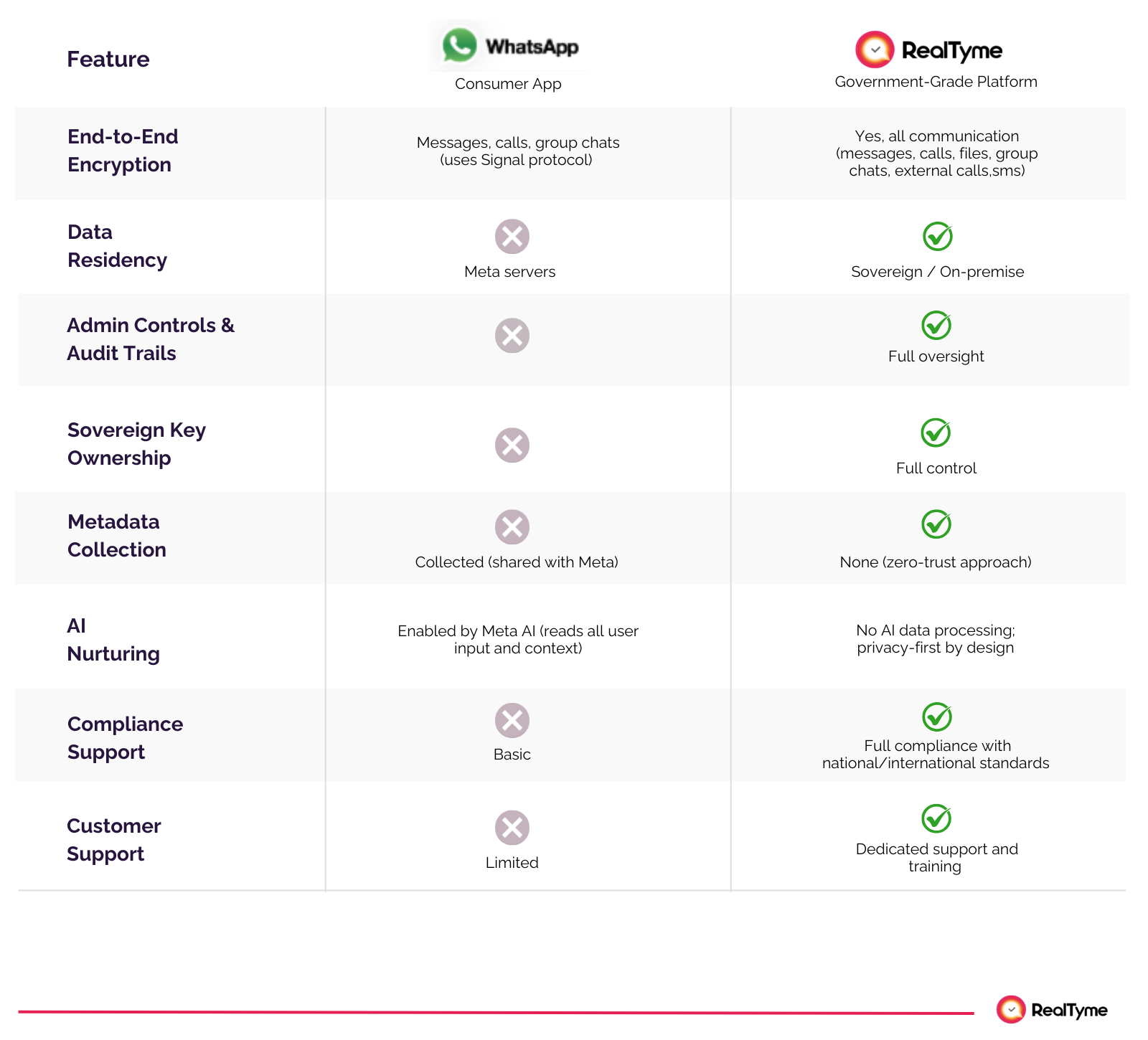
Comparison Table: WhatsApp vs. RealTyme for Sovereign Communication
When Convenience Becomes a Liability: Shadow Messaging in Government
Despite official mandates and security protocols, WhatsApp remains widely used across government bodies. Why? Because it’s easy.
This informal, unauthorized use of consumer-grade apps for professional duties is a growing trend known as “shadow messaging”, a term that mirrors the well-known concept of shadow IT.
Why Shadow Messaging Happens
- Operational Pressure - During crises or rapid-response situations, officials reach for tools they know. If official systems are slow, outdated, or hard to access, WhatsApp becomes the default fallback.
- Poor Usability of Official Systems - Government-issued platforms often prioritize security over experience, resulting in clunky, unresponsive apps that frustrate users. When usability is compromised, people bypass policy.
- Mobile and Remote Work Needs - As more government operations shift to mobile environments, from diplomatic missions abroad to emergency field teams, traditional desktop-bound systems fail to keep up. WhatsApp, by contrast, is fast, mobile-ready, and always connected.
The Risk: Policy Failure
When tools are not aligned with how officials actually work, even the strongest cybersecurity policy fails. The human tendency to prioritize convenience over compliance creates massive exposure risks.
The Solution: Secure AND Usable Tools
RealTyme was built to fill this exact gap, combining enterprise-grade, sovereign security with user-first design. Its interface is familiar, its performance is responsive, and its deployment options are flexible enough to operate under stress, from command centers to remote diplomatic posts.
The Hidden Risks of Metadata Exposure in Government Messaging
Encryption protects content, but metadata tells the story. In intelligence, defense, and diplomatic work, metadata can be just as damaging as leaked messages.
What is Metadata?
Metadata refers to the "data about the data." In messaging apps, this includes:
- Who sent the message
- To whom it was sent
- When and where it was sent
- How often the parties communicate
- Device and location information
Why Metadata Exposure is Dangerous
- Reveals Operational Patterns - If a foreign actor can track who your defense ministry talks to, and when, they can infer meetings, negotiations, crises, or policy shifts.
- Enables Target Profiling - Patterns of communication can identify key figures, relationships, and even expose undercover agents or informants.
- Legal Vulnerabilities - Under laws like the U.S. CLOUD Act, companies like Meta can be legally compelled to share metadata with U.S. authorities, even if the government using WhatsApp is a foreign sovereign.
RealTyme: Full Metadata Sovereignty
RealTyme avoids this vulnerability by enabling metadata to remain entirely within national control. Governments can configure retention, access, and audit policies to meet local regulations with no third-party exposure.
What Sovereign Communication Means for Governments
Sovereign communication is more than security. It’s about complete jurisdictional control.
Requirements for a Sovereign and Secure Communication Platform
- Data Residency Options - The platform must be deployable on-premises, in a government cloud, or within a nationally compliant private cloud infrastructure.
- Government-Controlled Encryption Keys - All cryptographic operations should be under national authority, with no third-party access to keys.
- Auditable, Transparent Infrastructure - Administrators must be able to trace, audit, and verify communication logs, not just message content, but user behavior and system events.
- Strong Authentication & Identity Control - Integration with national ID, military-grade PKI, or zero-trust frameworks is essential for validating users and protecting access.
- CLOUD Act Awareness - Governments must avoid platforms that fall under U.S. jurisdiction, where data or metadata can be subpoenaed without national oversight.
Secure vs Sovereign: A Critical Distinction
Many platforms claim to be secure. But if they:
- Store data on foreign infrastructure
- Do not offer sovereign key control
- Allow opaque metadata collection
- Or fall under U.S. legal jurisdiction
...then they are not sovereign, and thus not appropriate for government use.
Introducing RealTyme: The Most Trusted Sovereign and Secure Communication Platform
RealTyme is designed from the ground up for secure, sovereign, and compliant communication, trusted by public agencies, intelligence services, and international institutions.
Why Governments Trust RealTyme:
- Government-Owned Encryption Keys - Encryption and decryption are managed entirely by the government’s own infrastructure.
- Full Data Residency Control - Choose on-premise hosting, Swiss sovereign cloud, or your national government cloud provider.
- Multi-Format Secure Communication - RealTyme supports secure chat, voice, video, file transfer, and broadcast messaging.
- Granular Administrative Tools - Define access roles, audit trails, and real-time activity monitoring.
- Zero-Trust Architecture - Assumes breach and continuously verifies trust, ideal for high-risk environments.
- Air-Gapped Support - Operates in isolated networks for defense, intelligence, or mission-critical deployments.
.png)
Why Governments Must Prioritize Sovereign Platforms Like RealTyme
The risks of sticking with consumer-grade, non-sovereign apps are mounting:
- Unauthorized surveillance
- Diplomatic fallout
- Breach of citizen privacy
- Legal penalties
- Loss of control over national infrastructure
In contrast, sovereign platforms like RealTyme offer protection, compliance, and strategic advantage. Beyond tech, it’s about trust ensuring that no foreign power or corporation stands between a government and its communication.
Across Europe, Africa, and the Middle East, governments are adopting sovereign platforms as part of broader digital sovereignty strategies, moving away from U.S.-owned cloud and communication services.
When you weigh the cost of a breach (which can run into tens of millions) or regulatory fines against the strategic investment in sovereign infrastructure, the ROI becomes self-evident.
Conclusion
WhatsApp may be encrypted, but it is not sovereign. It cannot guarantee control over data, infrastructure, or jurisdiction, making it a risky choice for any government serious about national security.
RealTyme provides the sovereign foundation governments need: secure communication, full data ownership, and compliance alignment.
Act now before the next breach.
Book a demo or request a free communication risk assessment today to see how RealTyme can transform your government’s digital communication infrastructure.


