Why Out-of-Band Management Matters for Secure Internal Communication

In a world where cyberattacks and system outages are becoming more frequent and sophisticated, businesses cannot afford to rely solely on traditional communication channels.
When your main network goes down or gets compromised, how do your teams stay connected? How do you keep critical systems running and information flowing without exposing sensitive data?
The answer lies in Out-of-Band Management (OOB) — a strategic approach that provides a separate, secure communication path dedicated to managing and maintaining your IT infrastructure.
According to IBM, effective communication during cyberattacks and IT incidents can dramatically shorten resolution times and improve overall incident management.
One way companies achieve this is through Out-of-Band Management solutions, which provide a secure, dedicated network for teams to collaborate seamlessly, even when primary systems are down.
It’s a vital component for confidential internal collaboration, uninterrupted service delivery, and the ability to adapt quickly during crises.
The market is responding: the global out-of-band authentication sector grew to $1.5 billion in 2024 and is forecast to reach $7.5 billion by 2033—an impressive 18.7% CAGR—underscoring how organizations are investing heavily in Out-of-Band Management strategies.
What Is Out-of-Band Management?
Out-of-Band Management is the practice of controlling network devices, servers, and communication systems through an alternative, independent channel separate from the main production network.
Think about your primary network as your main highway — handling the day-to-day traffic. Out-of-Band Management is like having a private emergency lane that only authorized personnel can use, ensuring uninterrupted control even when the highway is jammed or closed.
You could also think of it as a satellite phone during a blackout, rarely used in normal operations, but a lifesaver when everything else is silent.
This secondary channel is typically isolated from the primary network and often uses dedicated hardware like console servers, modems, or cellular backup systems.
The goal is simple: maintain management access regardless of the state of your core infrastructure.
Why Traditional Communication Channels Fall Short
In most organizations, internal communication depends on a single, primary network infrastructure — email, instant messaging, VoIP, video conferencing, and cloud collaboration.
Recent Out-of-Band (OOB) Authentication Market Trends highlight the growing emphasis on secure, independent communication channels as a core element of modern cyber resilience strategies.
While effective for daily operations, these tools share critical weaknesses:
Single Point of Failure
When all communication flows through the same network, any disruption, from hardware failure, cyberattack, or natural disaster, can halt both collaboration and system control.
Security Vulnerabilities
Shared infrastructure exposes management traffic to the same risks as operational data. Attackers gaining network access can intercept commands, move laterally, or exfiltrate sensitive data.
Limited Crisis Response
If the primary network is down, alerts may not reach IT teams in time, remote access to devices can be impossible, and staff may fall back on insecure personal tools, creating confusion and risking misinformation.
These limitations make it clear: relying only on your primary network is a gamble.
How Out-of-Band Management Transforms Secure Internal Communication
Out-of-Band Management overcomes these weaknesses by providing a physically or logically separate communication path for management and emergency coordination.
1. Reliable Communication When It Matters Most
Out-of-band management creates a dedicated pathway for emergency communication and control. During outages or cyber incidents:
- IT admins can access servers, routers, and switches even if the main network is down.
- Decision-makers and on-site teams stay aligned minute-by-minute, avoiding confusion from compromised tools.
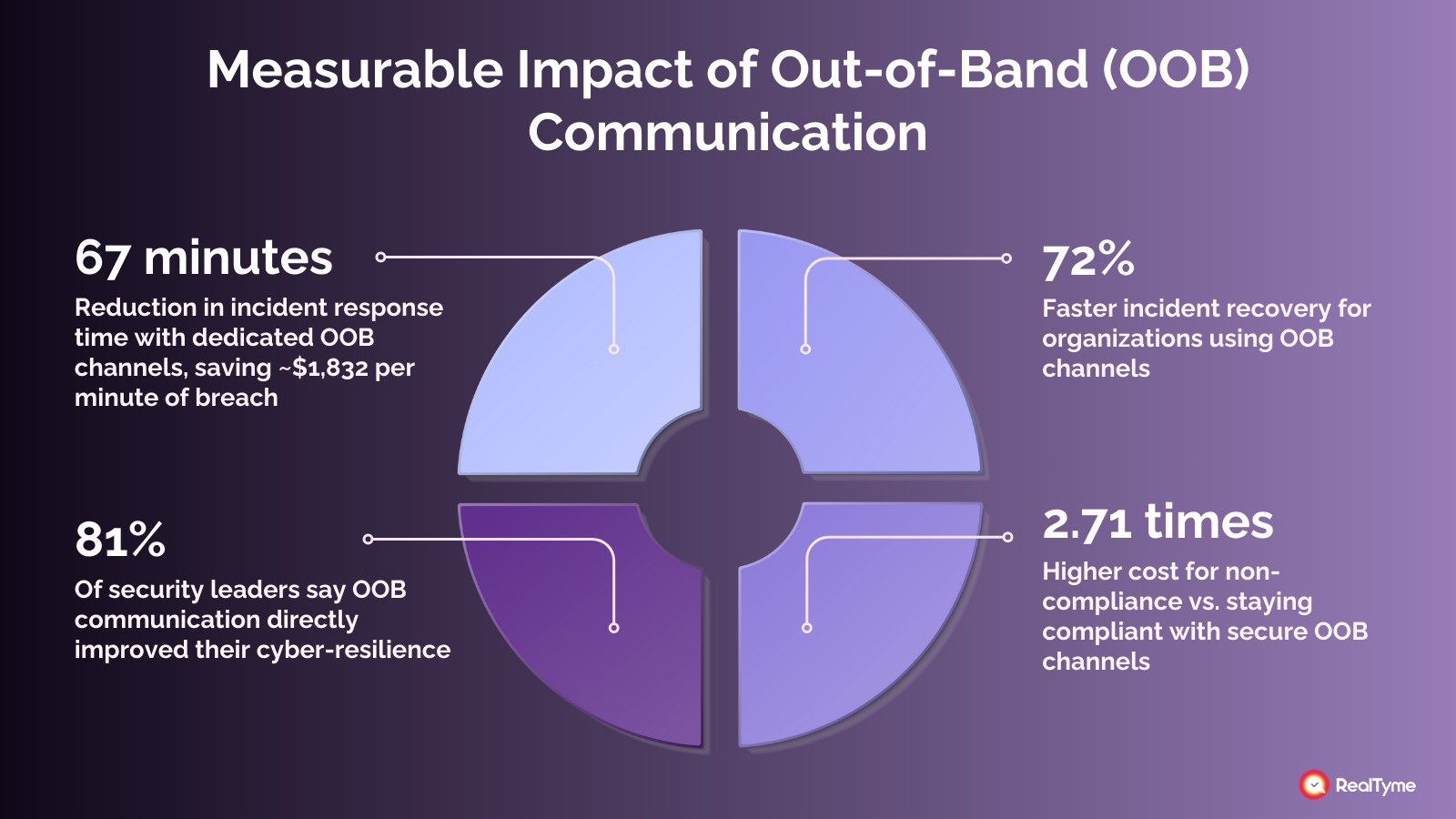
- Rapid action minimizes downtime — Gartner estimates downtime can cost $5,600 per minute for large enterprises.
2. Enhanced Security and Reduced Risk
Out-of-band communication channels are isolated from the main network, often protected by strict access controls and encryption. This separation:
- Prevents attackers from intercepting management traffic through compromised infrastructure.
- Limits the attack surface, since the OOB channel is invisible to standard network pathways.
- Helps meet compliance obligations, such as GDPR’s mandate for demonstrable safeguards in data handling.
3. Supports Business Continuity and Disaster Recovery
Out-of-Band Management is not just about secure messaging, but a cornerstone of business resilience. By guaranteeing management access in any scenario, businesses can:
- Maintain uptime and customer-facing services during IT failures.
- Accelerate disaster recovery by enabling remote troubleshooting and configuration.
- Avoid contractual penalties from missed SLAs and costly on-site interventions.
4. Facilitates Secure Collaboration Across Teams
Out-of-band communication channels also support coordinated response across IT, security, and leadership during emergencies. This means:
- Encrypted messaging and voice communication stay outside vulnerable networks.
- Cross-border teams in different risk environments can still operate as one unit.
- Sensitive decisions remain confidential, even under active attack conditions.
Real-World Scenarios
When implemented well, OOB Management turns theoretical resilience into real operational survival:
- Government & Defense Operations – During cyberattacks or communication blackouts, secure OOB channels allow military commands and government agencies to maintain operational control, coordinate sensitive missions, and issue emergency directives without exposing critical data.
- Healthcare Ransomware Attack – Patient systems are locked, but OOB channels let staff coordinate via secure messaging, IT isolate infected devices, and operations continue without shutdown.
- Natural Disaster – Floods or fires destroy local infrastructure, but cellular or satellite OOB links deliver evacuation orders to field teams within 15 minutes.
- Critical System Updates – Risky configurations are performed via OOB to avoid lockouts if updates fail.
- Financial Institution Under Cyberattack – Leadership and IT contain a breach through OOB messaging, restoring services while maintaining public trust.
- Transportation Network Failure – Train signaling goes offline, but OOB channels enable remote rerouting, preventing delays and accidents.
- Energy Plant Outage – A power plant maintains 99.98% grid uptime using OOB messaging during a core network failure.
- Municipal Emergency – City services coordinate disaster response via OOB, keeping communications running when the main network fails.
RealTyme: One Example of Secure Out-of-Band Messaging Platform
When it comes to Out-of-Band Management, the right technology partner can mean the difference between scrambling and executing a coordinated plan.
One example is RealTyme, a secure collaboration platform with built-in OOB capabilities.
RealTyme is engineered for environments where data sovereignty and uncompromised control are non-negotiable. Its design supports true out-of-band management, ensuring leadership, IT, and field teams can coordinate securely, even under complete network disruption.
Similar solutions from other vendors also exist, but RealTyme offers:
- Dedicated, independent communication channels outside the primary network, enabling operational continuity during outages or cyber incidents.
- End-to-end and at-rest encryption with quantum-resistant algorithms, defending against both current and emerging threats.
- Zero-trust architecture with strict identity verification and role-based access controls.
- Flexible, sovereign deployment options — on-premises, private cloud, or Swiss-based sovereign cloud — keeping all data under your jurisdiction and away from foreign control.
- Advanced administrative oversight with centralized policy enforcement, logging, and audit capabilities for regulatory compliance.
This combination of out-of-band readiness and data sovereignty makes it a strategic fit for governments, defense organizations, and regulated industries where communication security is operationally critical.
How to Implement Out-of-Band Management for Secure Internal Communication
Implementing Out-of-Band Management effectively is a critical step toward ensuring secure, resilient internal communication. It requires careful planning, the right technology choices, and ongoing governance.
Below is a comprehensive roadmap to help you build a robust Out-of-Band Management strategy tailored to your organization’s needs.
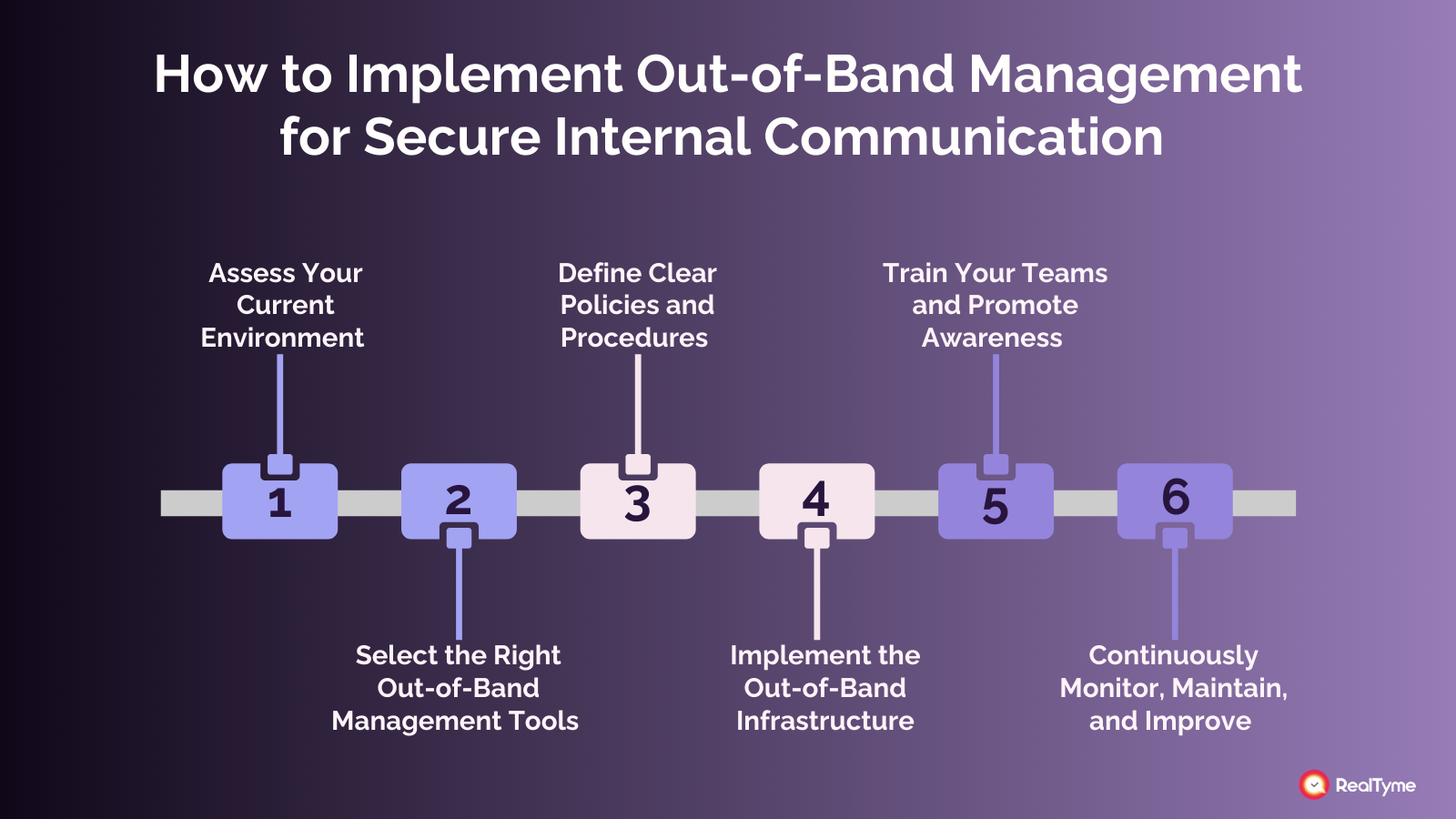
Step 1: Assess Your Current Environment and Identify Critical Assets
Start by conducting a thorough audit of your IT infrastructure and communication workflows to determine:
- Critical Systems: Identify which devices and applications require uninterrupted management access. This typically includes routers, switches, firewalls, servers, and communication platforms.
- Vulnerabilities and Single Points of Failure: Map out where your current communication and management systems rely on shared infrastructure, creating risks if that infrastructure goes down.
- Existing Communication Channels: Review current messaging tools and protocols to understand where out-of-band communication can supplement or replace vulnerable channels.
- Compliance Requirements: Note any industry-specific regulations (e.g., HIPAA, GDPR, PCI DSS) that mandate secure communication or audit trails.
This assessment will help you prioritize what needs OOB management first and set the scope for your implementation.
Step 2: Select the Right Out-of-Band Management Tools and Technologies
Choosing the right tools is foundational for secure out-of-band communication. Consider the following when evaluating options:
1. Hardware vs. Software Solutions:
- Hardware: Dedicated console servers, serial console devices, or cellular modems provide physical network separation. They are reliable but can be costlier and require physical setup.
- Software: Secure messaging platforms with out-of-band capabilities leverage secondary communication paths, such as encrypted messaging apps using cellular or satellite networks. These are more flexible and scalable.
2. Network Isolation and Security Features:
Ensure the OOB solution offers a truly separate communication path, preventing crossover with your primary network. It should include:
- End-to-end encryption (AES 256-bit or higher)
- Multi-factor authentication (MFA) for all users
- Role-based access controls to limit permissions
- Automated logging and audit trails for all communications and commands
3. Reliability and Redundancy:
The solution should maintain uptime during power failures or network outages, possibly incorporating backup power supplies (UPS), cellular failover, or satellite connections.
4. Integration Capabilities:
It’s beneficial if your out-of-band communication tools integrate seamlessly with existing IT management platforms (e.g., SIEM, ITSM) to streamline monitoring and incident response.
Step 3: Define Clear Policies and Procedures
Having tools isn’t enough without clear rules and guidelines to govern their use.
Your policies should cover:
- Access Management: Specify who can access the OOB channels, under what circumstances, and through which authentication methods. Limit access to essential personnel only.
- Usage Scenarios: Define explicit scenarios that warrant switching to out-of-band communication (e.g., network outage, security breach, hardware failure) to avoid misuse or unnecessary activation.
- Incident Response Protocols: Integrate out-of-band management into your incident response playbooks. Detail how communication should flow, which teams are involved, and what tools are used to coordinate actions.
- Monitoring and Auditing: Set up continuous monitoring of OOB channels for unauthorized access attempts or anomalies. Regularly review logs and conduct audits to ensure compliance and detect potential issues.
- Training and Drills: Incorporate Out-of-Band Management procedures into regular training sessions and simulate outage scenarios to test readiness and improve response times.
Step 4: Implement the Out-of-Band Infrastructure
With plans and policies in place, proceed to the practical setup:
- Deploy Hardware Components: Install and configure console servers, cellular modems, or other physical OOB devices at key network points. Ensure physical security measures (e.g., locked cabinets, surveillance) are applied.
- Configure Network Isolation: Set up a dedicated management network that is physically or logically isolated from the production network. Use VLANs, firewalls, or separate physical cables as needed.
- Install and Integrate Software Tools: Roll out secure messaging platforms and management consoles configured with appropriate encryption, authentication, and access controls.
-Test Failover Capabilities: Simulate primary network failures to validate that out-of-band channels remain operational and accessible. Verify remote access capabilities from off-site locations.
Step 5: Train Your Teams and Promote Awareness
No technology can succeed without people who know how to use it effectively.
Training should include:
- Hands-On Workshops: Teach IT staff, security teams, and leadership how to access OOB channels, operate management consoles, and escalate incidents properly.
- Clear Communication: Inform all relevant employees about when and how OOB channels will be used, emphasizing the importance of following protocols during emergencies.
- Ongoing Education: Keep teams updated on any changes to OOB tools or procedures. Encourage reporting of issues or suggestions for improvements.
Step 6: Continuously Monitor, Maintain, and Improve
Out-of-band management is not a one-and-done project. To keep your secure internal communication resilient:
- Regular Audits - Periodically review system logs, access controls, and incident reports to detect vulnerabilities or misuse.
- Update Tools - Patch and upgrade OOB hardware and software promptly to protect against new security threats.
- Refine Policies - Adjust procedures based on lessons learned from drills or real incidents.
- Test Often - Conduct scheduled failover and disaster recovery drills to ensure everyone remains proficient with out-of-band channels.
Implementing a comprehensive Out-of-Band Management strategy will give your business a trusted communication backbone that operates when everything else fails.
It’s an investment in resilience, security, and seamless collaboration that can save your company time, money, and reputation when it matters most.
Final Thoughts
In the next cyber incident, every minute without coordination could cost your business thousands. Out-of-Band Management is more than a backup communication method. It’s a strategic advantage that empowers businesses to maintain secure internal communication no matter what challenges arise.
With cyber threats escalating and IT environments growing more complex, relying on a single network for all communication is a risk few can afford.
Investing in OOB management not only safeguards your infrastructure but also fortifies your team's ability to respond, collaborate, and keep operations running smoothly.
Is your business ready to embrace the power of out-of-band management?
Try RealTyme today and experience secure, independent collaboration that keeps your teams connected, even when everything else goes down.



