Why Mobile and Desktop Applications Are a Major Security Concern?

Today, mobile and desktop applications power nearly every aspect of our personal and professional lives—from banking and healthcare to collaboration and communication. But this convenience comes at a cost: applications are increasingly exploited as entry points for cybercriminals, putting sensitive personal and business data at risk.
A recent ENISA report highlights that applications are among the top attack vectors in Europe, with vulnerabilities leading to data breaches, ransomware incidents, and compliance violations.
Whether it’s mobile apps downloaded from app stores or enterprise software on corporate desktops, the risks are real and growing.
Why Applications Are Highly Targeted by Cybercriminals
Applications both mobile and desktop serve as gateways to a wealth of sensitive data. This includes personal identifiers (names, addresses, ID numbers), financial information (bank accounts, payment details), and confidential business communications (emails, internal reports, project documents). Because applications often consolidate so much critical information, they are prime targets for cyber attackers, who exploit vulnerabilities to gain access, steal data, or disrupt operations.
Some of the most common risks include:
- Data leakage through poorly secured APIs: Applications frequently rely on Application Programming Interfaces (APIs) to communicate with servers, third-party services, or other apps. Weak authentication, lack of encryption, or exposed endpoints can allow attackers to intercept or manipulate sensitive data. For example, a misconfigured API could expose user emails or payment details to unauthorized parties.
- Malware injection in mobile or desktop environments: Cybercriminals often target applications to deliver malware that can compromise devices, steal credentials, or grant remote access. Mobile apps can be modified or repackaged with malicious code, while desktop applications may be exploited via vulnerabilities in outdated software versions.
- Unauthorized access due to weak authentication mechanisms: Apps that rely solely on passwords or have poor session management are at higher risk. Attackers can exploit weak or reused passwords, session hijacking, or inadequate token expiration to gain unauthorized access. Multifactor authentication (MFA) is a critical mitigation strategy.
- Hidden vulnerabilities from third-party dependencies: Many applications integrate third-party libraries, SDKs, or plugins for added functionality. While convenient, these dependencies may introduce unpatched vulnerabilities or hidden backdoors. Attackers can exploit these weaknesses even if the main application itself is secure.
The impact of an application-related breach goes far beyond immediate financial losses:
- Regulatory compliance violations: Breaches can trigger penalties under frameworks like GDPR or other European data protection regulations. Non-compliance may result in fines, legal action, or mandatory audits.
- Reputation damage: Customers, partners, and investors may lose trust in an organization that cannot protect sensitive information, affecting brand value and business relationships.
- Erosion of user trust: Users expect their personal and professional data to be secure. Once compromised, it can be difficult to regain confidence, impacting adoption of applications and long-term engagement.
Applications consolidate sensitive data, rely on multiple systems, and often have complex architectures. Without robust security measures, they represent one of the most significant cyber risk vectors for organizations today.
Mobile Security Threats: Protecting Apps, Networks & Devices
Smartphones, particularly iPhones, are no longer just communication tools; they’re essential for work, finance, and daily life. But their ubiquity also makes them high-value targets for cybercriminals.
From sneaky malware in apps to intercepted data over networks, and even attacks directly on the device itself, threats can appear anywhere. That’s why understanding mobile security at three critical levels app, network, and device is essential for keeping your data and business safe.
1. App-Level Threats: The Most Common Gateway for iOS Cyberattacks
Applications are the primary entry point for cybercriminals targeting mobile devices. Even though Apple enforces a rigorous App Store review process and tight security guidelines, vulnerabilities in apps remain a major concern.
Attackers often exploit these weaknesses to steal sensitive information, spread malware, or hijack device functions.
Data Leakage – One of the most pervasive threats at the app level is unauthorized data exfiltration. Studies show that 61% of iOS applications leak user data, often without the user’s explicit consent. This includes personal information, location data, and even behavioral patterns that can be exploited for targeted attacks.
Hardcoded Secrets – Developers sometimes embed sensitive credentials, such as API keys or authentication tokens, directly into the app’s code. This practice creates a serious vulnerability: research indicates that 71% of iOS apps leak at least one secret, which attackers can exploit to access backend systems, cloud storage, or private databases.
Malicious or Compromised Apps – Even seemingly legitimate apps can carry hidden threats. A notable example includes the "Fitness Balance" and "Calories Tracker" apps, which were removed from the App Store in 2018 after tricking users into authorizing fraudulent TouchID payments. These incidents illustrate that cybercriminals often disguise malicious functionality within trusted apps, making detection difficult even for vigilant users.
Why App-Level Threats Matter
With over 90% of mobile device usage occurring within apps , these vulnerabilities make applications the most frequent target for attackers. Organizations and individual users must therefore prioritize mobile app security, including regular updates, app monitoring, and the use of mobile threat defense (MTD) solutions to detect and block malicious behavior.
Key takeaway: App-level vulnerabilities ranging from data leakage and hardcoded secrets to compromised applications represent a critical risk in iOS security, making proactive defenses essential for anyone relying on mobile devices for personal or business use.
2. Network-Level Threats: Intercepted Communications and Hidden Dangers
Even the most secure iOS device can be compromised if network security is weak. Network-level threats target the data in transit between mobile devices and servers, making interception, manipulation, and eavesdropping possible.
These attacks are particularly dangerous because they often bypass device-level protections and exploit human behavior or misconfigured applications.
Man-in-the-Middle (MitM) Attacks – One of the most common network-level threats, MitM attacks occur when an attacker secretly intercepts communication between a user and a server. On iOS, poorly coded apps that fail to validate SSL/TLS certificates are especially vulnerable. Attackers can capture sensitive data, inject malicious content, or redirect users to phishing sites without triggering alerts. According to Positive Technologies, 23% of mobile apps lack proper encryption safeguards, leaving critical information exposed.
Unsecured Wi-Fi Networks – Public Wi-Fi networks are a frequent target for cybercriminals. Attackers can create rogue access points that mimic legitimate networks, tricking devices into connecting. Once connected, devices are susceptible to eavesdropping, credential theft, and session hijacking. Even iOS devices, which encrypt traffic by default, are not immune if users access sensitive apps without additional safeguards.
Phishing and Smishing Over Networks – Network threats are not limited to technical exploits. Cybercriminals often leverage phishing emails or smishing (SMS-based phishing) campaigns that redirect users to malicious websites over mobile networks. These attacks can harvest Apple IDs, passwords, or banking credentials without requiring malware installation. The Verizon 2023 Data Breach Investigations Report found that 74% of breaches involved human-targeted attacks, with phishing as one of the primary methods.
Why Network-Level Threats Matter
Mobile users frequently connect to public or untrusted networks, often without realizing the risk. Even with a secure device, weak network practices can expose sensitive corporate or personal data. Organizations need to implement VPNs, encrypted communication protocols, and secure Wi-Fi policies, while users must be educated to avoid risky network behavior.
Key takeaway: Network-level attacks, including MitM, unsecured Wi-Fi exploitation, and phishing over networks, demonstrate that protecting the connection between devices and servers is as critical as securing the device itself. Effective mobile cybersecurity requires vigilance, encryption, and strong network hygiene.
3. Device-Level Threats: Exploiting the Hardware and Operating System
Even the most secure apps and networks cannot fully protect a mobile device if the hardware or operating system is compromised. Device-level threats target iOS itself, exploiting vulnerabilities in the operating system, hardware, or physical access points.
These attacks are particularly dangerous because they often allow attackers to bypass traditional security controls.
Zero-Click Exploits and Spyware – Advanced malware, such as NSO Group’s Pegasus, has demonstrated the power of zero-click exploits on iOS devices. These attacks can compromise a device without requiring user interaction, allowing attackers to access calls, messages, location data, microphone, and camera. Pegasus has been used in targeted espionage against journalists, activists, and corporate executives, highlighting the severity of device-level threats.
Jailbreaking – While jailbreaking an iPhone can provide extra customization, it also removes many of Apple’s built-in security protections. Jailbroken devices are more susceptible to malware, unauthorized app installation, and privilege escalation attacks, putting sensitive corporate and personal data at risk.
Physical Theft and Unauthorized Access – Losing a mobile device or having it stolen is a significant security concern. Without strong authentication, such as passcodes, Face ID, or Touch ID, sensitive information stored on the device including emails, business apps, and passwords can be accessed. Even devices with encryption can be vulnerable if attackers gain physical access and exploit known vulnerabilities.
Outdated iOS and Unpatched Vulnerabilities – Apple regularly releases updates to patch security flaws, yet devices that remain outdated or unpatched are prime targets for attackers. Exploits targeting unpatched vulnerabilities can allow attackers to bypass device controls, install spyware, or steal sensitive data without detection.
Why Device-Level Threats Matter
Device-level attacks often have the highest potential impact, as they can compromise the entire mobile environment, including apps, network traffic, and stored data. Protecting the device itself is therefore critical to a comprehensive mobile security strategy.
Protection Tips:
- Keep iOS updated to the latest version to patch vulnerabilities.
- Enable strong authentication (Face ID, Touch ID, or complex passcodes).
- Avoid jailbreaking your device.
- Use remote wipe features to erase data if the device is lost or stolen.
Key takeaway: Device-level threats underscore that securing apps and networks is not enough. Protecting the iOS device itself—through updates, strong authentication, and vigilance against physical threats is essential for complete mobile security.
The European Perspective on Application Security
European regulators recognize that applications both mobile and desktop pose unique security and privacy risks. Unlike traditional websites, apps often store sensitive data locally, access device features, and integrate with third-party services.
To address these challenges, authorities such as ENISA (European Union Agency for Cybersecurity) and the European Data Protection Board (EDPB) provide detailed guidance for developers, publishers, and organizations to build secure, privacy-compliant applications.
Key Principles for Secure Applications
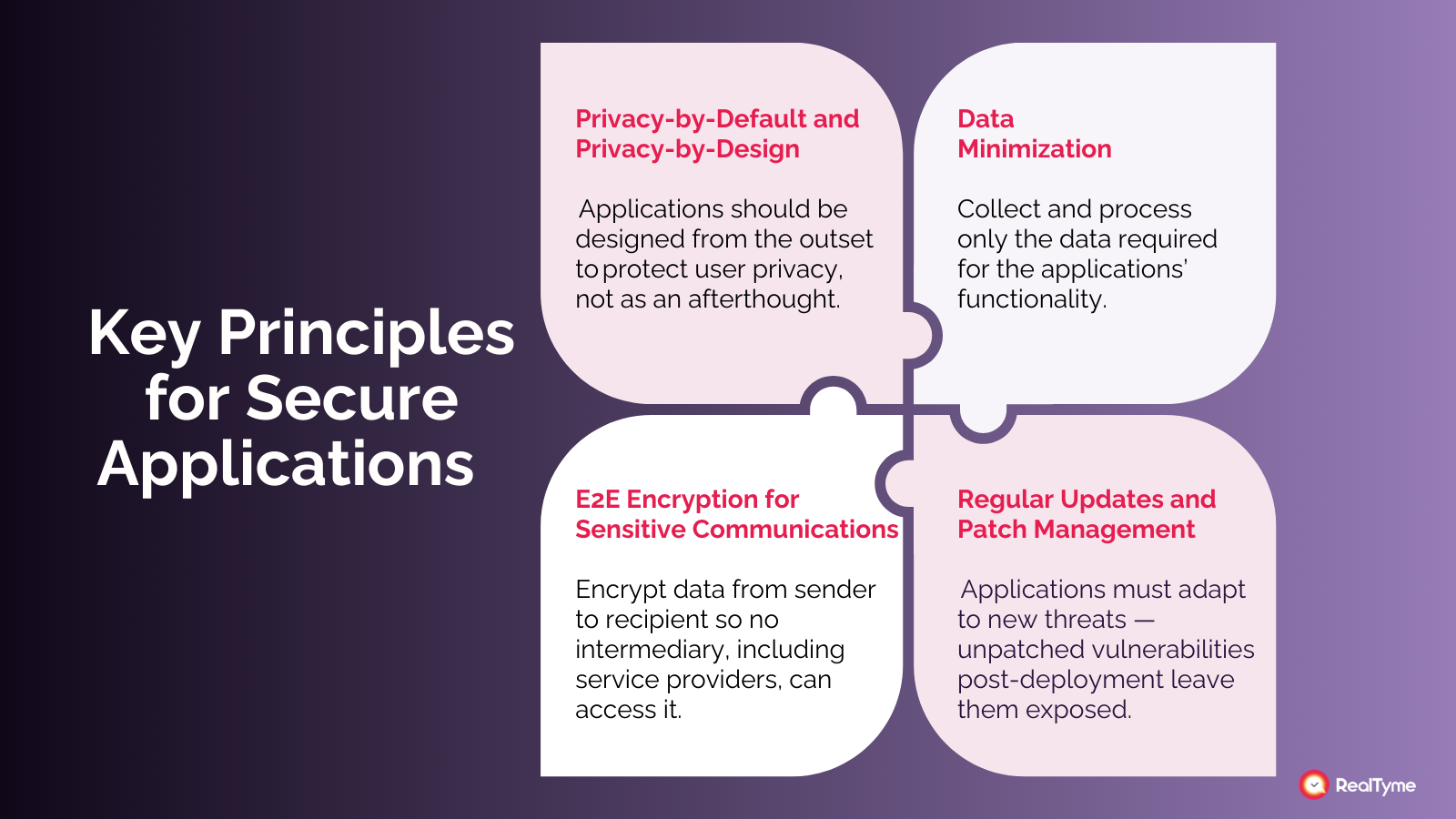
1. Privacy-by-Default and Privacy-by-Design
Concept: Applications should be designed from the outset to protect user privacy, not as an afterthought.
Practical Steps:
- Limit data collection to what is strictly necessary.
- Configure default settings to maximize privacy (e.g., location sharing off by default).
- Apply encryption for both stored and transmitted data.
Benefit: Users gain confidence knowing their data is automatically protected, reducing accidental leaks.
Learn more: 5 Ways for GDPR-Compliant Messaging in Government and Critical Sectors
2. Data Minimization
Concept: Collect and process only the data required for the app’s functionality.
Practical Steps:
- Avoid requesting sensitive permissions unless essential.
- Aggregate or anonymize data wherever possible.
- Regularly review and purge unnecessary or outdated data.
Benefit: Reduces impact of potential breaches and aligns with GDPR principles on personal data processing.
3. End-to-End Encryption for Sensitive Communications
Concept: Encrypt data from sender to recipient so no intermediary—including service providers—can access it.
Practical Steps:
- Use strong cryptographic standards (e.g., AES-256).
- Ensure keys are securely stored on user devices, not in centralized servers.
- Regularly rotate encryption keys and update cryptographic libraries.
Benefit: Protects sensitive communications against interception, man-in-the-middle attacks, and unauthorized access.
4. Regular Updates and Patch Management
Concept: Applications must evolve to defend against emerging threats. Vulnerabilities discovered post-deployment can be exploited if unpatched.
Practical Steps:
- Maintain a security patch cycle with rapid deployment for critical vulnerabilities.
- Monitor third-party libraries and SDKs for updates.
- Automate updates where possible to ensure users always have the latest secure version.
Benefit: Reduces exposure to known exploits and strengthens overall application resilience.
Why This Matters
By following these European best practices, organizations can:
- Ensure compliance with GDPR and other EU regulations.
- Reduce the risk of costly data breaches and fines.
- Build trust with users and business partners by demonstrating a privacy-first, security-conscious approach.
- Strengthen overall cybersecurity posture across mobile and desktop applications.
Building Secure Communication Applications
This is where RealTyme takes a distinctive approach. Unlike many mainstream platforms that rely on data monetization models, our solution is built with sovereignty, privacy, and compliance at its very foundation.
Every interaction on RealTyme, whether through mobile applications or desktop clients is protected with end-to-end encryption, granular access controls, and a compliance-ready architecture that adapts to evolving European and global regulations.
Why is this important?
Applications today sit at the center of the cybersecurity discussion. As highlighted by European regulators such as ENISA and the EDPB, mobile and desktop apps pose unique risks: they often store sensitive data locally, integrate with third-party services, and access device features that could expose users to privacy violations or breaches if left unsecured.
Without a security-by-design approach, organizations face not only operational risks but also serious compliance fines and reputational damage.
At RealTyme, we bridge this gap by embedding privacy-first principles into our platform. Instead of treating compliance as an afterthought, we design every feature to align with data protection by design and by default.
Whether you are safeguarding critical government communications, managing confidential business discussions, or enabling secure collaboration across borders, RealTyme provides the trusted environment to do so without compromise.
In today’s world where applications are both indispensable and increasingly targeted, RealTyme stands apart as a sovereign, compliant, and human-centric alternative. With us, secure communication is not an added layer it is the very core of the experience.



