5 Ways for GDPR-Compliant Messaging in Government and Critical Sectors

Across Europe’s government offices, emergency coordination centers, and critical infrastructure - from energy grids to public health agencies, messaging is moving faster, more informally, and with greater risk. But we rarely stop to ask whether our communication infrastructure is truly compliant with the laws we defend.
This is especially true when it comes to messaging.
From encrypted chats between civil protection teams during flood response, to confidential updates passed between intelligence branches, to routine messages exchanged with EU citizens on vaccination eligibility or tax deadlines, these messages carry not just information, but obligations. Legal, ethical, and operational obligations.
The General Data Protection Regulation (GDPR), enacted to safeguard citizens’ data and digital dignity, is not only a legal framework. It’s a litmus test for how seriously institutions take the privacy and trust of those they serve. And nowhere is that more fragile, or more exposed, than in the unstructured, lightly governed world of digital messaging.

What follows is not a checklist. It’s a reflection on five fundamental pillars that must underpin any GDPR-compliant messaging ecosystem for governments and critical national sectors, each drawn not from abstract theory, but from hard-learned lessons on the front lines of public service.
1. Messaging Must Respect the Boundaries of Purpose
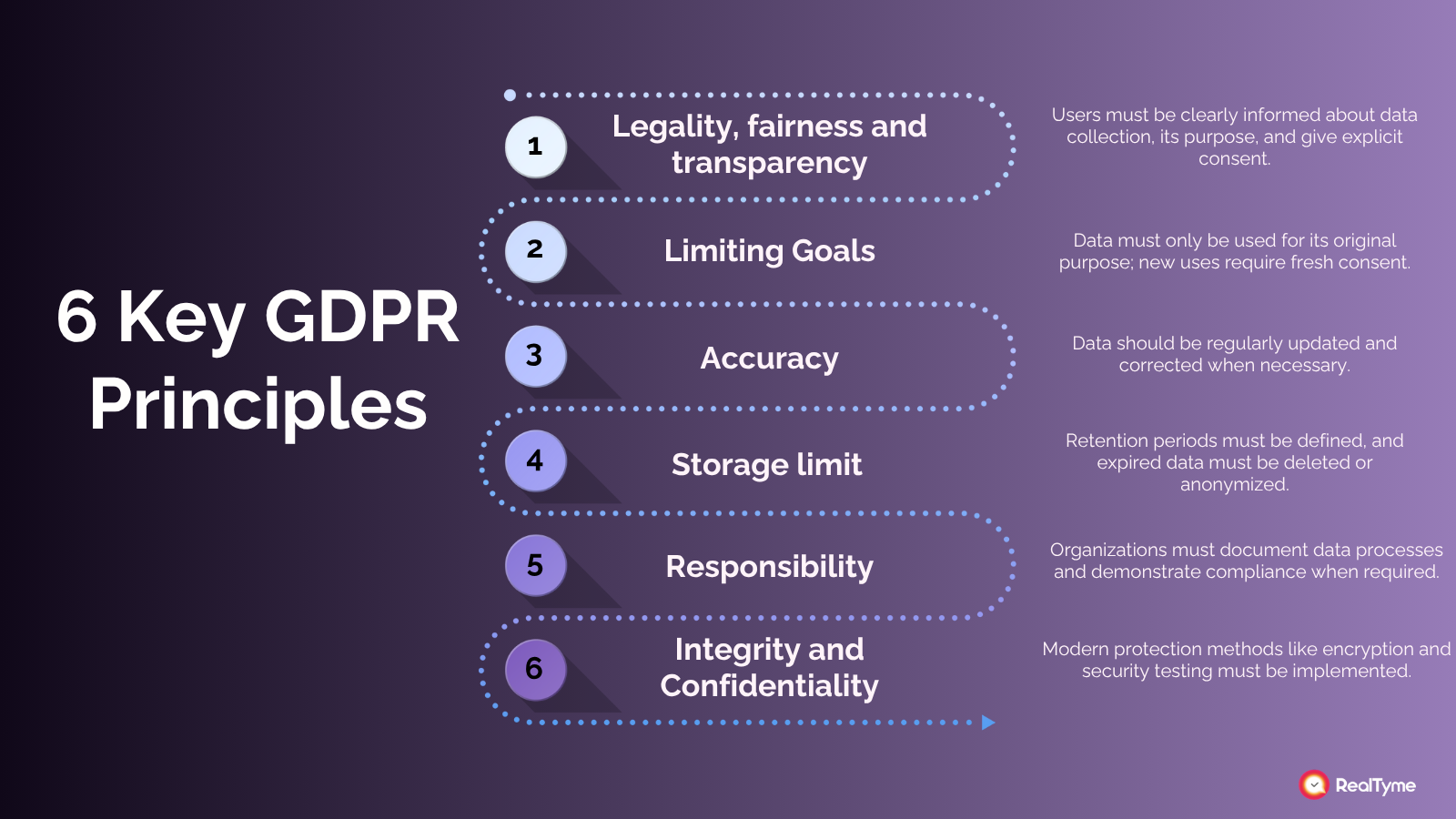
One of the foundational principles of GDPR is purpose limitation: data must be collected for a clearly defined reason, and it must not be used beyond that scope.
But in the rush of daily operations, it’s easy to forget this. A citizen submits their mobile number to receive SMS alerts during a regional blackout. Months later, that same number is used to send a satisfaction survey or an update on unrelated public services.
In commercial environments, this might be written off as a marketing error. In the public sector, it becomes something far more serious—a breach of institutional trust.
GDPR does not allow silent repurposing. Even if the intention is well-meaning, the law is clear: without explicit, informed consent for each use case, messaging becomes unlawful.
More than policy, this principle requires embedded workflows. Messaging systems must enable use-specific tagging of personal data, audit trails for consent, and expiration of rights.
Government institutions must adopt a culture where consent isn’t buried in forms but tracked and enforced dynamically, ensuring every communication has a defensible, documented reason.
Shadow IT and the Risks of Unsanctioned Messaging
When sanctioned messaging tools are outdated or hard to use, staff turn to consumer messaging apps out of frustration. WhatsApp, Signal, or Telegram become the default, not because they’re secure, but because they’re fast, familiar, and outside oversight.
This phenomenon, often called "shadow IT," creates one of the most dangerous blind spots for GDPR compliance.
These messaging apps may be encrypted, but they are not governed. They may protect content, but they do not protect metadata. And they certainly don’t offer the oversight, control, or auditability that public institutions require.
Worse, they enable the silent buildup of fragmented communications—data silos spread across personal devices, outside of institutional control or protection.
The solution isn't punishing users. It's understanding why they turned away in the first place and building secure, compliant systems that are actually usable.
GDPR compliance starts with trust in the tools provided.
2. The Infrastructure Beneath the Message Matters as Much as the Message Itself
You can write the most thoughtful, compliant message in the world. But if it travels through infrastructure that stores it outside the EU, indexes it for machine learning, or allows third-party access, you’ve already failed GDPR.
This is the hidden trap of modern messaging platforms. Many are built for scale and speed, not privacy or sovereignty. Data travels through opaque networks, stored on servers subject to foreign jurisdiction, where even metadata—who messaged whom, when, and from where—can be legally accessed by non-EU governments.
In critical sectors like defense, public health, and finance, this is a national security risk.
True GDPR-compliant messaging means owning the data flow. It means knowing exactly where your messages are processed, who can access them, and whether any foreign legal framework could compel that access.
Some organizations have tried to patch this with contractual protections or standard clauses. But those are paper shields. The only real defense is architectural: platforms designed from the ground up for sovereignty and compliance.
What 'Privacy by Design' Actually Looks Like in Messaging
Under GDPR, privacy by design is a legal requirement. But too often it’s treated as a feature, not a foundation.
In messaging, privacy by design means:
- Only collecting what is necessary, no default metadata logging.
- Let users define how long messages persist.
- Giving organizations full visibility into data flows without granting unrestricted access.
- Encrypting everything, not just content, but also the metadata.
A compliant and secure communication platform should:
- Allow self-hosting or sovereign cloud hosting.
- Never rely on analytics or behavioral profiling.
- Provide tools to enforce policies like message lifespan, retention, and access revocation.
3. Metadata Is the Silent Breach You Never See Coming
We often think of data breaches as dramatic events: servers hacked, files leaked, passwords compromised. But in the world of messaging, the most dangerous exposures are often invisible.
It’s not the content of the message, but the context.
When was it sent? From what device? To whom? At what frequency? Was it read? Was it forwarded?
Individually, these fragments seem harmless. But when aggregated, they reveal patterns of movement, hierarchy, timing, even personal behaviors. In intelligence work, this is called traffic analysis. In GDPR, it’s called profiling, and it demands either explicit consent or a lawful exemption.
Unfortunately, most messaging apps don’t just collect this metadata, they hoard it. Sometimes for diagnostics. Sometimes for analytics. Often just because they can.
For GDPR-compliant messaging in critical environments, metadata must be treated as first-class personal data. It must be minimized, encrypted, and subject to the same lifecycle rules as the content itself.
This requires systems designed to forget by default, not remember forever.
The Human Factor: Training, Habits, and Responsibility
Even the most advanced messaging infrastructure can be undermined by simple human error.
A forwarded file. A screenshot shared externally. An unintentional upload to the wrong chat.
Every public institution must treat data protection not only as a compliance issue but as a behavioral one. This means:
- Regular GDPR-awareness training tailored to roles;
- Clear internal protocols for secure communication
- User interfaces that guide, not just allow, responsible choices
In messaging, the interface is the policy. And every user is a data processor.
4. Oversight Without Overreach: The Delicate Balance of Transparency
In public institutions, transparency is important. You must be able to demonstrate who accessed what, when, and under what authority. When an audit happens, or worse, when a breach must be explained, you need a clear, defensible trail.
But transparency does not mean omniscience.
GDPR insists that oversight must be proportional. System administrators can’t be free to inspect private messages on a whim. Logs must exist, but they must be sealed, selectively accessible, and tamper resistant. Users must retain the dignity of privacy, even under the umbrella of state or enterprise scrutiny.
This is a hard line to walk, and most communication platforms fall off one side or the other. Either they provide too little visibility to be auditable, or too much access to be compliant.
The right approach is cryptographic: secure enclaves, zero-trust principles, role-based access. Logs must be tied to governance, not convenience. Infrastructure must be designed to empower both users and administrators, without privileging one over the other.
GDPR Messaging Isn’t One Size Fits All
The principles of GDPR are universal, but the operational realities of public service are not.
A police department needs secure real-time alerts. A public hospital needs patient confidentiality at a scale. A nuclear plant needs strict access logs with immutable audit trails.
These needs are radically different. Messaging platforms must reflect that.
A one-size-fits-all solution either over-engineers controls for some users or under-delivers for others. Instead, public institutions need systems that can be:
- Configured per department or unit;
- Tailored to different threat models and data sensitivities;
- Scalable without compromising governance.
The strength of GDPR messaging lies in specificity.
Beyond Compliance: Messaging as Institutional Memory and Human Risk
Laws like GDPR ask institutions to protect data. But what they rarely say out loud is this: data is often most vulnerable not in the hands of systems, but in the hands of people.
And messaging, informal, fast, improvisational, is where that risk plays out most acutely.
During a crisis, decisions are made in seconds. Teams improvise, coordinate, document, and share. Field operatives text coordinates. Emergency managers forward PDFs. Ministers approve statements on the move. The line between official and unofficial channels blurs.
When the dust settles, these messages become the only record of what was said, what was done, and why. They form the basis of institutional memory. And if they’re not preserved responsibly, that memory collapses, either into chaos or into scandal.
Too much deletion, and you lose the ability to investigate or learn. Too much retention, and you create a data lake vulnerable to leaks, breaches, or misuse.
The solution is intentional messaging architecture: secure communication platforms that allow institutions to define what gets kept, who sees it, for how long, and under what justification.
GDPR compliance is about preserving truth without compromising dignity.
5. The Moment of Breach Is the Moment of Truth
No system is perfect. Breaches will happen. And when they do, GDPR doesn’t just ask you to report them. It asks you to understand them, explain them, and take accountability within 72 hours.
This is where many messaging platforms fall apart. Logs are incomplete. User data is fragmented. Third-party vendors are unresponsive. Deletion isn’t really deletion, just soft removal.
A true GDPR-compliant messaging ecosystem must be incident-ready. That means breach response isn’t an afterthought but embedded into the very architecture of the communication platform.
You must be able to:
- Reconstruct the scope of the incident with clarity.
- Identify which individuals were affected.
- Prove what data was accessed or extracted.
- Delete compromised data fully and permanently.
- Communicate with affected parties quickly and respectfully.
If your communication platform can’t support this level of response, then your organization is carrying out a silent liability, one that will only surface when it’s too late to prepare.
The Cost of Non-Compliance Is Rising—Sharply
In 2023 alone, data protection authorities across the EU issued approximately €2.1 billion in GDPR-related fines. That’s more than the combined total of fines issued in 2019, 2020, and 2021, a clear signal that enforcement is no longer symbolic.
Regulators are not just watching but acting. For government agencies and critical sectors entrusted with sensitive data, this escalation underscores a hard truth: privacy failures are fiscal liabilities with legal consequences.
A Secure Communication Platform Built for This Moment: Why RealTyme Matters
Most messaging apps were not built for public service. They were built for scale, convenience, and engagement. They treat privacy as a settings menu, not a founding principle.
RealTyme is different.
Designed for sovereign, compliant, and secure communication, RealTyme is used by governments, defense networks, and mission-critical industries where silence is safer than exposure and where GDPR isn’t a ceiling, but a floor.
It doesn’t track users. It doesn’t hoard metadata. It doesn’t send data across borders or embed third-party analytics.
What it does is offer:
- Sovereign deployment: Self-hosting or trusted national cloud hosting with no foreign dependency;
- End-to-end encryption: With local key control, no backdoors;
- Privacy by design: Metadata is minimized, encrypted, and purged by default;
- Compliant audit logs: Secure, sealed logs without compromising message content;
- Response-ready tooling: From breach impact mapping to user notifications.
RealTyme isn’t trying to reinvent communication. It’s trying to restore integrity to it, especially where it matters most: in public service and critical missions.
It’s not just compliant. It’s trustworthy.
What to Ask When Evaluating Messaging Platforms
When assessing whether your communication platforms meet the real demands of GDPR and public sector integrity, ask these questions:
- Where is our message data stored and who has legal jurisdiction over it?
- What metadata is collected, and can we control or erase it?
- Can we enforce data retention limits, message expiry, and consent tracking?
- Are breach response and audit logs built-in or bolted on?
- Can we host this platform ourselves or with a sovereign cloud provider?
If your answers raise more questions than clarity, it’s time to reassess your messaging architecture.
Final Thoughts: GDPR Compliance as Democratic Practice
In the end, GDPR is not just about rules. It’s about values.
It’s about whether a government respects the boundaries of its citizens’ data. Whether a utility operator understands the power it holds, not just over infrastructure, but over information. Whether public service is conducted with discipline, not just convenience.
Messaging might seem like a footnote in this bigger story, but it isn’t. It’s the connective tissue of the modern state. And if that tissue is porous, everything it connects becomes vulnerable.
So, the question is not whether your messaging is fast. Or convenient. Or user-friendly.
The question is: Is it worthy of public trust?
Let’s Take the Next Step
To learn how RealTyme supports GDPR-compliant, sovereign messaging for public institutions and critical sector operators, contact us here.
We’ll help you assess your current messaging risks and build an ecosystem worthy of the trust placed in you by your citizens.
Because in the world you operate in, silence must be safe, speech must be secure, and trust must be earned, message by message.


