How Secure Communication Protects Government Data

Government agencies are responsible for safeguarding some of the nation’s most sensitive information, from classified intelligence to citizen records.
These institutions whether in central government, defense, or the wider public sector are prime targets for hackers and cybercriminals seeking to exploit vulnerabilities in government communication systems.
The stakes could not be higher. A single breach can compromise national security, erode public trust, and jeopardize the integrity of sensitive data. That’s why investing in secure communication for government agencies is not just a precaution it’s a necessity.
In this blog, we’ll explore why secure communication is essential for protecting government operations, how it defends against cyber threats, and the role of advanced systems in ensuring data sovereignty, resilience, and confidentiality in the digital era.
Why Secure Communication is Critical for Government Agencies
Secure communication refers to the use of technologies and practices that ensure information shared between authorized parties remains confidential, authentic, and tamper-proof.
This includes safeguarding phone calls, instant messages, emails, file transfers, and video conferencing against interception, unauthorized access, and manipulation.
At its core, secure communication is about ensuring that sensitive information travels only between the people who are meant to receive it and no one else.
For government agencies, the importance of secure communication cannot be overstated. Unlike private businesses, governments manage not only organizational data but also classified intelligence, citizen records, law enforcement operations, and critical infrastructure strategies.
These assets make them some of the most attractive targets for cybercriminals, hacktivists, and state-sponsored attackers.
When communication channels are compromised, the consequences extend far beyond data loss:
- National security is jeopardized when classified military or intelligence information is leaked.
- Public trust erodes if citizens’ personal data falls into the wrong hands.
- Essential government services are disrupted, especially during crises such as natural disasters, pandemics, or national emergencies when reliable communication is most critical.
- Geopolitical stability is threatened, as intercepted communications can be weaponized for disinformation or espionage.
In today’s landscape, where governments are constantly under digital siege, relying on unsecured or commercial-grade platforms introduces unacceptable risks.
That’s why implementing secure messaging and communication platforms tailored for government use is no longer optional, but a cornerstone of resilience, sovereignty, and operational continuity.
Read our blog post to learn more about the importance of secure internal communication for government agencies.
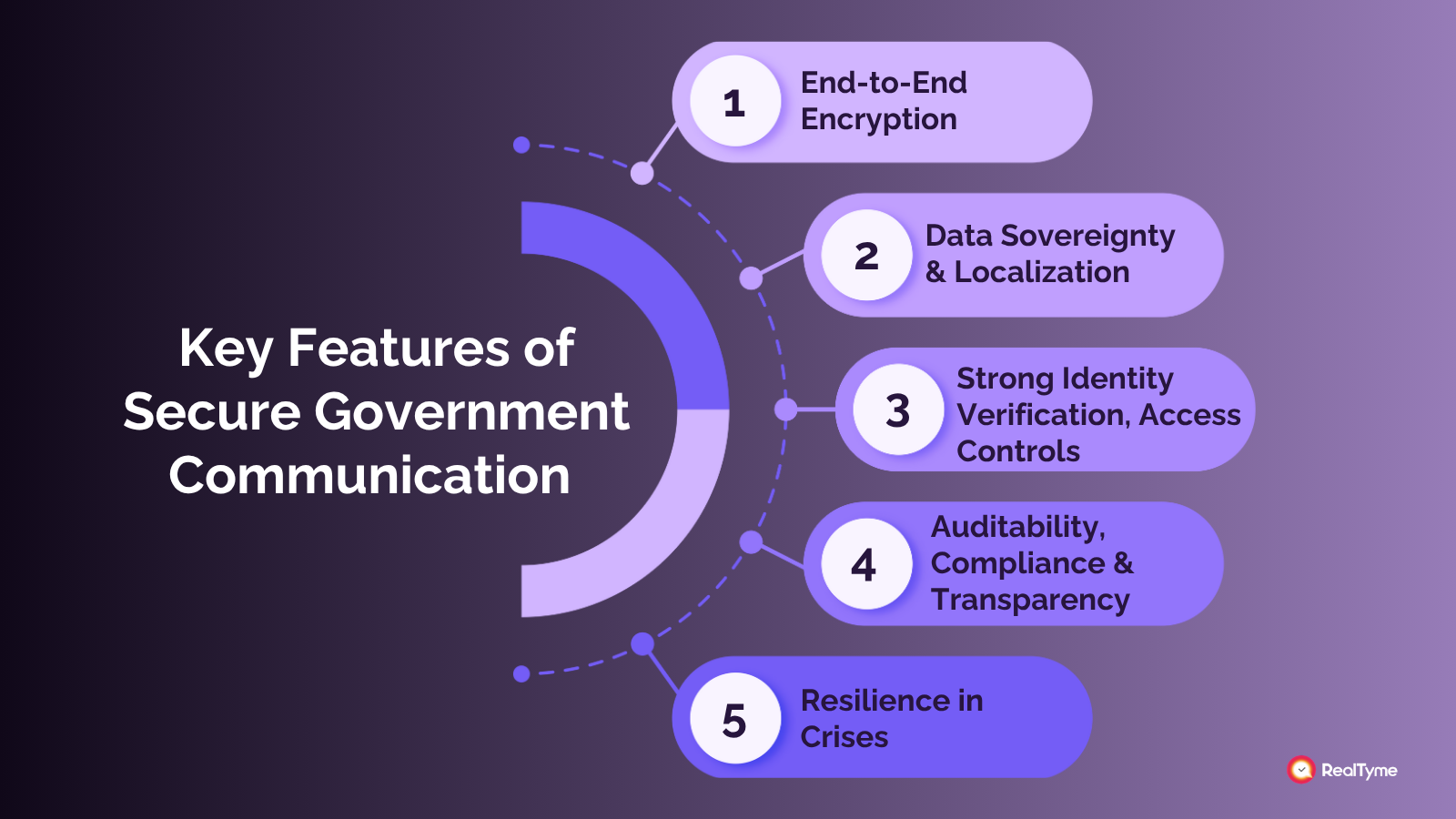
Key Features of Secure Government Communication Platforms
A secure government communication platform does far more than simply encrypting messages.
To effectively protect sensitive information, government agencies need systems that combine advanced encryption, strict access control, data sovereignty, resilience, and auditability.
These multi-layered protections ensure that communications remain confidential, tamper-proof, and compliant with national security and privacy regulations.
In addition to safeguarding data, a robust platform helps governments maintain operational continuity, regulatory compliance, and public trust, even in the face of cyberattacks or emergency situations.
Below, we explore the essential features every government communication system should include, supported by real-world examples of how these measures protect national security and sensitive citizen data.
1. End-to-End Encryption (E2EE) for Confidentiality
What it means: End-to-end encryption ensures that all data whether messages, voice or video calls, or file transfers is encrypted on the sender’s device and can only be decrypted by the intended recipient.
This guarantees that no intermediaries, including service providers or network operators, can access or alter the content during transmission.
Why it matters: For government agencies, E2EE is a critical component of secure government communication. It prevents interception by hackers, malicious insiders, or other unauthorized parties.
Even if communications are captured, encrypted data remains unreadable without the correct cryptographic keys.
Across the globe, governments are increasingly recognizing the importance of E2EE. For example, the United States, European Union member states, and Australia have established policies and legislation that mandate strong encryption for transmitting sensitive information between agencies, including defense and intelligence communications.
Similarly, secure messaging platforms like Signal and WhatsApp have been evaluated for internal use in legislative and government contexts to provide encrypted channels for official communications, highlighting the practical adoption of E2EE in protecting classified government data and citizen information.
2. Data Sovereignty & Localization for Legal Compliance
What it means: Data sovereignty ensures that government communications are stored and processed within trusted national jurisdictions, under local legal and regulatory control. This includes protecting data from foreign surveillance laws and ensuring compliance with national privacy regulations.
Why it matters: For governments, maintaining control over sensitive information is critical for data protection, national security, and public trust.
Countries like Australia have implemented certified “strategic” data centers to host sensitive government records, while the European Union enforces GDPR standards that require strict local control of citizen data. Similarly, China’s Data Security Law mandates that critical information is stored domestically to safeguard national interests.
By ensuring data sovereignty, government agencies can prevent unauthorized access from external actors and maintain compliance with legal obligations.
3. Strong Identity Verification & Access Controls
What it means: Secure government communication platforms use robust authentication methods, including multi-factor verification and role-based permissions, to ensure that only authorized users can access sensitive channels.
Access rights are assigned based on the principle of least privilege and are regularly audited to prevent misuse.
Why it matters: Weak access control is one of the most common ways sensitive data is compromised. Governments worldwide have implemented strong identity verification to secure digital services.
For instance, the US uses Login.gov for secure authentication in federal digital services, while the Netherlands relies on Digidentity for citizens to securely access tax, social security, and other government services.
These measures help prevent unauthorized access, impersonation, and insider threats, ensuring that government messaging security remains uncompromised.
4. Resilience in Crises & Operational Continuity
What it means: Resilient communication systems are designed to remain secure and functional during emergencies, including cyberattacks, natural disasters, or geopolitical crises.
Features include redundant networks, secure offline modes, and disaster recovery protocols to ensure uninterrupted operations.
Why it matters: During crises, government agencies must continue to coordinate responses, manage public services, and make critical decisions.
Countries with dedicated emergency communication channels and redundant secure networks, including satellite-based systems for defense and civil protection, demonstrate the importance of resilience in maintaining operational continuity. Without these safeguards, even minor disruptions can compromise national security and public trust.
5. Auditability, Compliance & Transparency
What it means: Every action in a secure communication system message sent, file accessed, or permission granted should leave a traceable and tamper-proof record.
Regular audits and compliance checks ensure that communications meet national and international privacy, security, and cybersecurity standards.
Why it matters: Auditability allows governments to detect misuse, investigate breaches, and enforce accountability. Compliance with laws like GDPR in the EU or Australia’s digital security standards ensures legitimacy and reduces legal and reputational risks.
Governments implementing these standards demonstrate commitment to protecting sensitive information and maintaining public trust.
These features together form the foundation of robust government messaging security.
By integrating end-to-end encryption, data sovereignty, strong access control, operational resilience, and full auditability, governments can protect sensitive data, maintain public trust, and ensure continuity even under the most challenging circumstances.
Top Threats and Challenges Facing Government Communications Today
Despite the implementation of secure communication platforms, government agencies continue to face a myriad of cyber threats that jeopardize the confidentiality, integrity, and availability of sensitive information.
These threats are increasingly sophisticated, persistent, and damaging. Key challenges include:
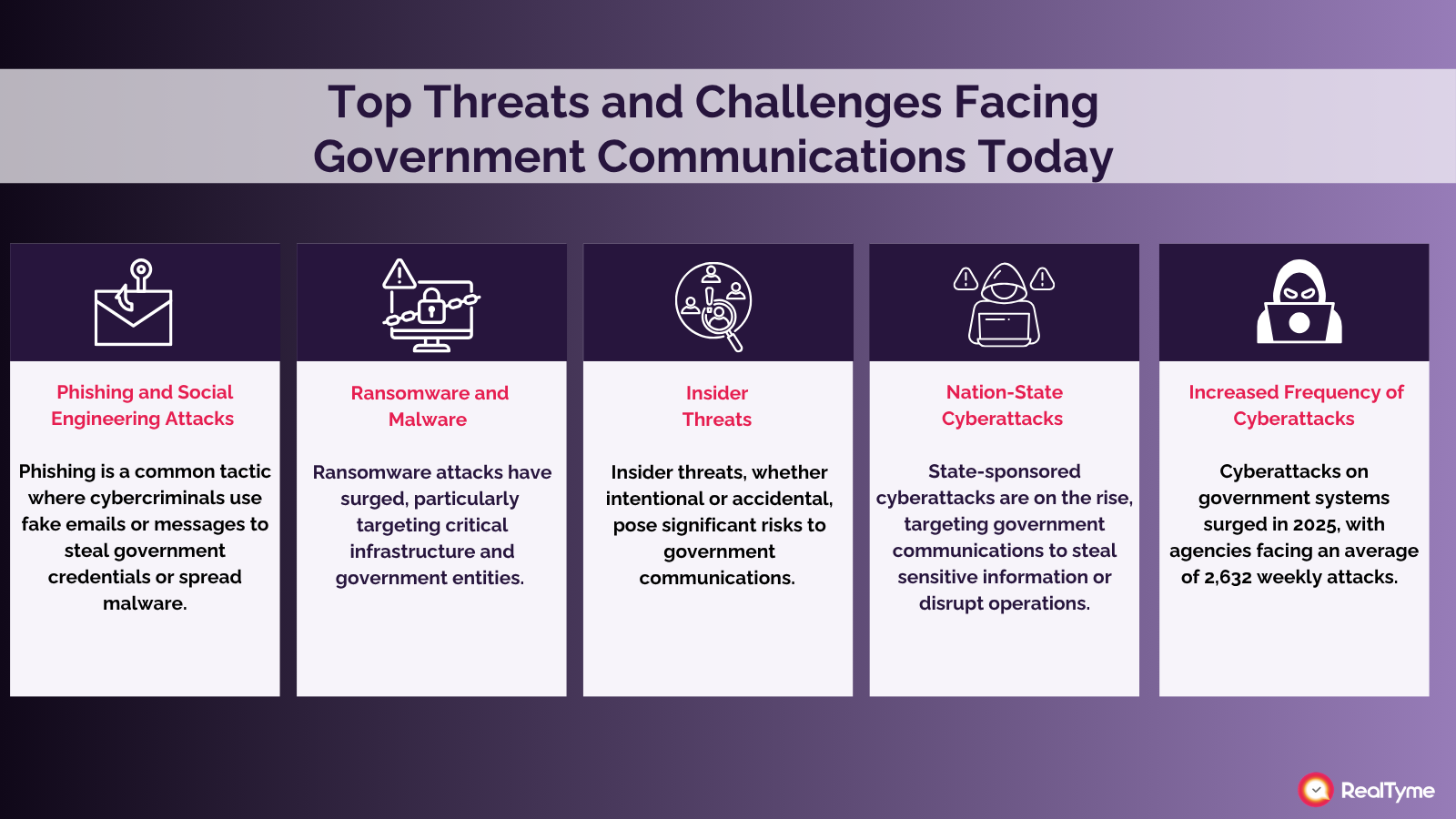
1. Phishing and Social Engineering Attacks
Phishing remains one of the most prevalent methods for cybercriminals to gain unauthorized access to government systems. Attackers often craft deceptive emails or messages that appear legitimate, tricking officials into revealing login credentials or downloading malicious attachments.
For instance, in 2024, the UK Met Office, along with other government agencies, blocked over five million phishing emails almost double the number from 2023.
2. Ransomware and Malware on Critical Infrastructure
Ransomware attacks have surged, particularly targeting critical infrastructure and government entities.
In 2024, the FBI reported a 9% increase in complaints about ransomware attacks on U.S. critical infrastructure compared to the previous year. These attacks often lead to significant operational disruptions and financial losses.
3. Insider Threats and Misuse of Access
Insider threats, whether intentional or accidental, pose significant risks to government communications. Personnel with access to sensitive systems may misuse their privileges, leading to data breaches or leaks.
A report by the U.S. Government Accountability Office highlighted that poor management of identities and access contributed to 75% of security failures in federal agencies by 2023.
4. Nation-State Cyberattacks and Espionage
State-sponsored cyberattacks are on the rise, targeting government communications to steal sensitive information or disrupt operations.
In 2024, Japan linked over 200 cyberattacks to the Chinese hacking group MirrorFace, which targeted national security and advanced technology data.
Similarly, the Czech Republic accused China of conducting a malicious cyber campaign against its Foreign Ministry, beginning in 2022.
5. Increased Frequency of Government Cyberattacks
The frequency of cyberattacks on government systems has escalated dramatically.
In the second quarter of 2025, public sector organizations experienced an average of 2,632 weekly cyberattacks each, marking a 26% year-over-year increase. This surge underscores the urgent need for robust and resilient communication platforms.
Best Practices for Implementing Secure Government Communication
Implementing secure communication for government agencies requires more than technology—it demands a strategic, multi-layered approach that combines policy, training, and advanced security solutions.
Adopting these best practices ensures that sensitive data, classified information, and citizen records remain protected from evolving cyber threats.
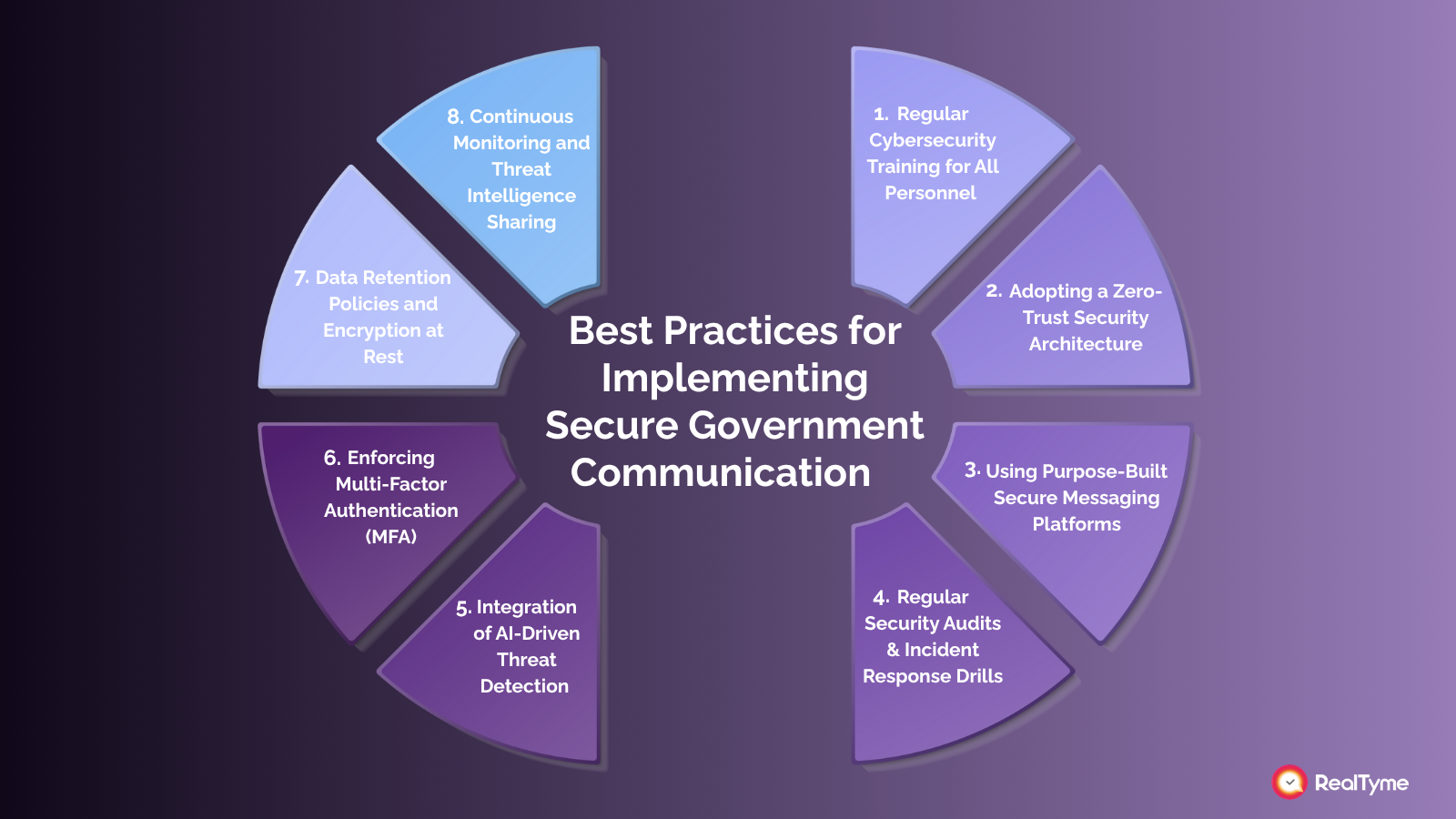
1. Regular Cybersecurity Training for All Government Personnel
Human error remains one of the leading causes of security breaches in government systems.
Comprehensive cybersecurity training programs help officials recognize phishing attempts, social engineering attacks, and suspicious activity. Training should be ongoing and scenario-based, including real-world simulations of cyberattacks targeting government messaging systems.
By fostering a culture of cybersecurity awareness, agencies strengthen their overall government communication security and reduce the risk of insider threats.
2. Adopting a Zero-Trust Security Architecture
A zero-trust security model assumes that no user or device is inherently trustworthy, even if they are inside the network perimeter. Every access request is continuously verified using authentication, authorization, and behavioral analytics.
Governments adopting zero-trust architectures significantly reduce the risk of unauthorized access and data breaches, especially in complex networks spanning multiple agencies, cloud platforms, and third-party partners.
This approach is critical for secure government messaging and data protection.
3. Using Purpose-Built Secure Messaging Platforms
Standard messaging platforms often lack the encryption, compliance, and administrative controls required for government use.
Purpose-built secure communication platforms for government offer end-to-end encryption, data sovereignty, access controls, and auditability.
They ensure that sensitive communications between ministries, defense agencies, and external partners remain confidential, tamper-proof, and fully compliant with national and international regulations.
4. Conducting Regular Security Audits and Incident Response Drills
Periodic security audits help identify vulnerabilities in government communication systems before they are exploited.
Combined with incident response drills, audits ensure agencies are prepared for ransomware attacks, insider threats, and other cyber crises.
These proactive measures improve resilience and continuity in government operations, while also supporting compliance with regulations like GDPR, national cybersecurity laws, and defense-specific security standards.
5. Integration of AI-Driven Threat Detection
Modern cyber threats are increasingly sophisticated, often leveraging automation and machine learning to evade traditional defenses.
Integrating AI-driven threat detection into government communication platforms allows agencies to identify suspicious activity in real time, detect anomalies, and respond quickly to potential breaches.
From advanced phishing detection to behavioral analytics on messaging platforms, AI ensures that sensitive government data is continuously monitored and protected.
6. Enforcing Multi-Factor Authentication (MFA)
Multi-factor authentication adds an extra layer of security, requiring users to verify identity using two or more independent credentials such as passwords, security tokens, or biometric verification.
MFA is particularly important for accessing government communication systems, where a single compromised password could jeopardize sensitive operations or classified information.
7. Data Retention Policies and Encryption at Rest
Beyond securing communications in transit, governments must ensure data stored within messaging systems and databases is encrypted and retained according to strict policies.
Encryption at rest, combined with clear retention schedules, ensures compliance with national regulations, reduces exposure in the event of breaches, and supports audit and accountability measures.
8. Continuous Monitoring and Threat Intelligence Sharing
Government agencies should implement continuous monitoring systems that track network activity, user behavior, and system logs for anomalies.
Additionally, sharing threat intelligence across departments and with international partners helps anticipate and mitigate emerging cyber threats.
This collaborative approach strengthens national cybersecurity resilience and protects sensitive government communications from evolving attacks.
Why Government Agencies Choose RealTyme
RealTyme is purpose-built to meet the unique security, compliance, and operational needs of government agencies:
- Private and self-hosted to maintain complete control over sensitive information.
- End-to-end encryption to safeguard classified communications.
- Data sovereignty compliance with national and international regulations.
- Operational resilience to ensure communication continues under any circumstances.
- Auditability and reporting for transparency and accountability.
By implementing RealTyme, governments can protect sensitive data, ensure continuity during crises, and reinforce public trust, all while complying with the most stringent security and regulatory requirements.
Take Control of Government Communications with RealTyme
In an era of rising cyber threats and increasing regulatory scrutiny, governments cannot afford to rely on standard messaging apps or legacy platforms.
RealTyme provides a secure, sovereign, and resilient solution that empowers government agencies to communicate confidently and protect sensitive information.
Secure your government communication today with RealTyme because the safety of classified information and citizen data cannot be compromised.



