Cybersecurity in 2025: How Secure Communication Became New Perimeter

As 2025 comes to a close, one reality has become unmistakable: cybersecurity is no longer defined by protecting a network, a data center, or a fixed set of systems.
Over the past year, organizations across every sector have experienced the same pattern. Major incidents, financial losses, regulatory exposure, and reputational damage were not caused by failed infrastructure alone, but by compromised conversations, manipulated identities, and decisions made under pressure.
The traditional security perimeter did not weaken in 2025.
It effectively disappeared.
Today, organizations are securing people, identities, conversations, and decisions that take place across devices, platforms, locations, and jurisdictions — often in real time, and often outside the visibility of traditional security controls. Sensitive information now moves through live calls, instant messages, crisis channels, and executive discussions where speed matters more than process.
By the end of 2025, it has become clear that secure communication is no longer a productivity feature. It is a core cybersecurity control, essential to operational resilience, regulatory compliance, and organizational trust.
The 2025 Threat Landscape: Faster, Smarter, More Human
The past year confirmed a fundamental shift in cyber risk.
Cyberattacks in 2025 were not just more sophisticated — they were more personal. Attackers increasingly targeted human behavior, exploiting moments of urgency, authority, and trust rather than relying solely on technical vulnerabilities.
One of the most significant developments observed throughout 2025 was the shift from infrastructure-focused attacks to communication-centric attacks.
- Ransomware attacks evolved well beyond data encryption. Many attacks deliberately disrupted internal communication, fragmented incident response coordination, and isolated leadership teams to maximize operational damage and leverage.
- Deepfake and impersonation attacks became operationally effective. AI-generated voices and messages convincingly mimicked executives, partners, and trusted contacts, leading to fraudulent transactions, data exposure, and policy bypasses.
- Shadow IT continued to expand under pressure. During incidents and time-critical decisions, employees defaulted to familiar consumer messaging apps, creating security and compliance blind spots.
- Regulatory and data sovereignty pressures intensified. Uncontrolled communication channels increasingly resulted in compliance violations, audit failures, and erosion of stakeholder trust.
Across these threats, one conclusion emerged repeatedly:
attackers no longer needed to breach secure systems if they could exploit insecure conversations.
In 2025, some of the most damaging security failures originated not from outdated technology, but from how and where critical communication took place.
Why Traditional Communication Tools Failed Under Pressure
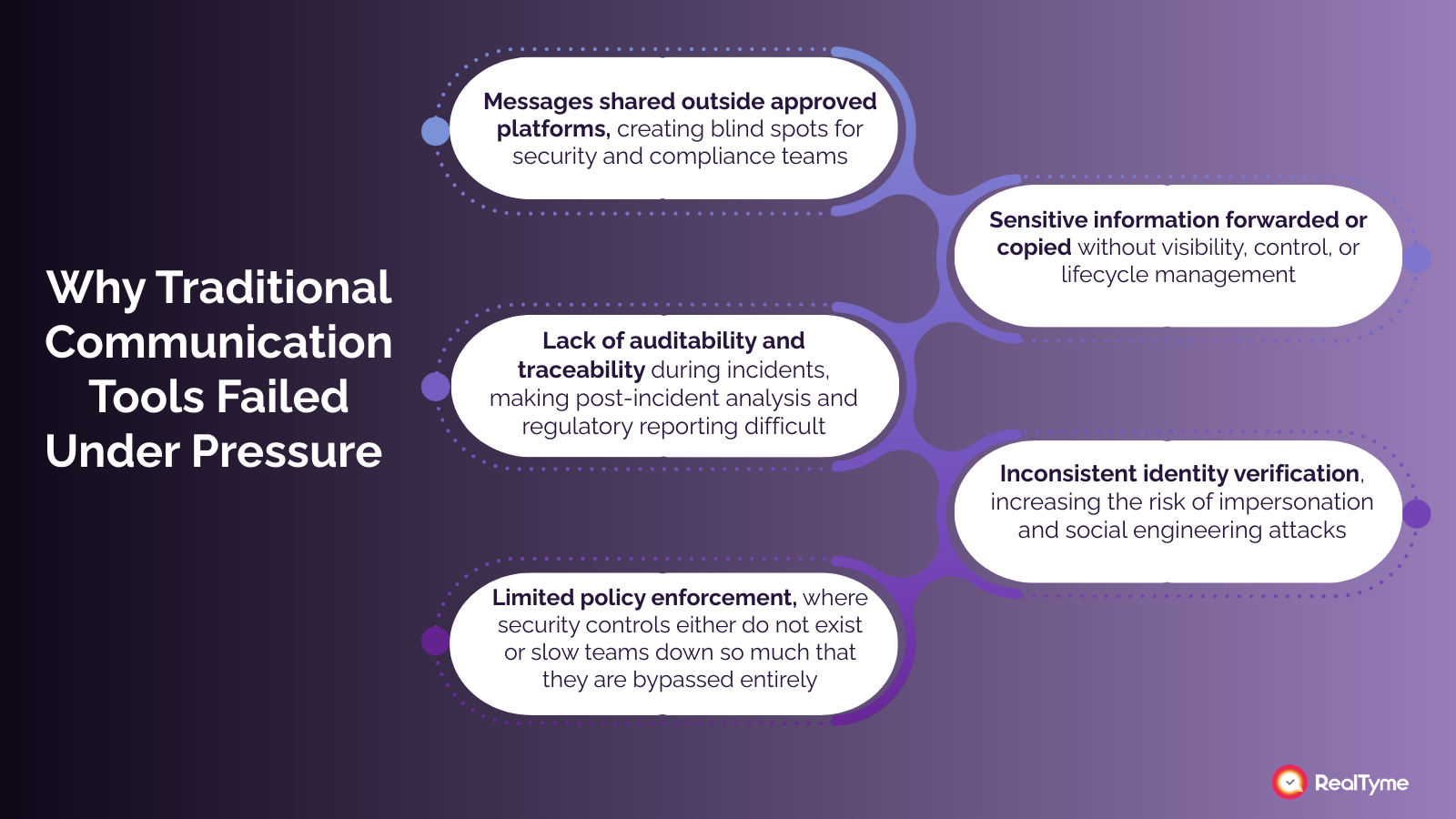
Email, consumer messaging apps, and mainstream collaboration platforms were never designed for security-critical communication.
Throughout 2025, organizations learned — often the hard way — that tools optimized for convenience and collaboration break down when conversations involve sensitive data, executive decisions, or regulated environments.
During cyber incidents, outages, or crises, employees naturally prioritized speed and familiarity. When secure tools introduced friction, they were bypassed. This behavior was predictable — and consistently exploited.
Common failure points included:
- Messages shared outside approved platforms, creating blind spots for security and compliance teams
- Sensitive information forwarded or copied without visibility, control, or lifecycle management
- Lack of auditability and traceability during incidents, making post-incident analysis and regulatory reporting difficult
- Inconsistent identity verification, increasing the risk of impersonation and social engineering attacks
- Limited policy enforcement, where security controls either do not exist or slow teams down so much that they are bypassed entirely
By the end of 2025, cybersecurity leaders reached a clear conclusion:
training and restrictive policies alone are ineffective.
Telling employees what not to use fails when secure alternatives are slower, harder, or less intuitive — especially under pressure.
The real challenge became strategic:
How do we make the secure way the fastest, easiest, and most natural way to communicate?
Secure Communication as a Core Cybersecurity Layer
By the close of 2025, secure communication had established itself as a foundational layer of modern cybersecurity architecture.
As organizations moved beyond perimeter-based defenses toward identity-driven and zero-trust models, communication emerged as one of the most exposed — and least protected — attack surfaces.
Secure communication now sits alongside identity management, endpoint protection, and incident response as a core pillar of cyber resilience.
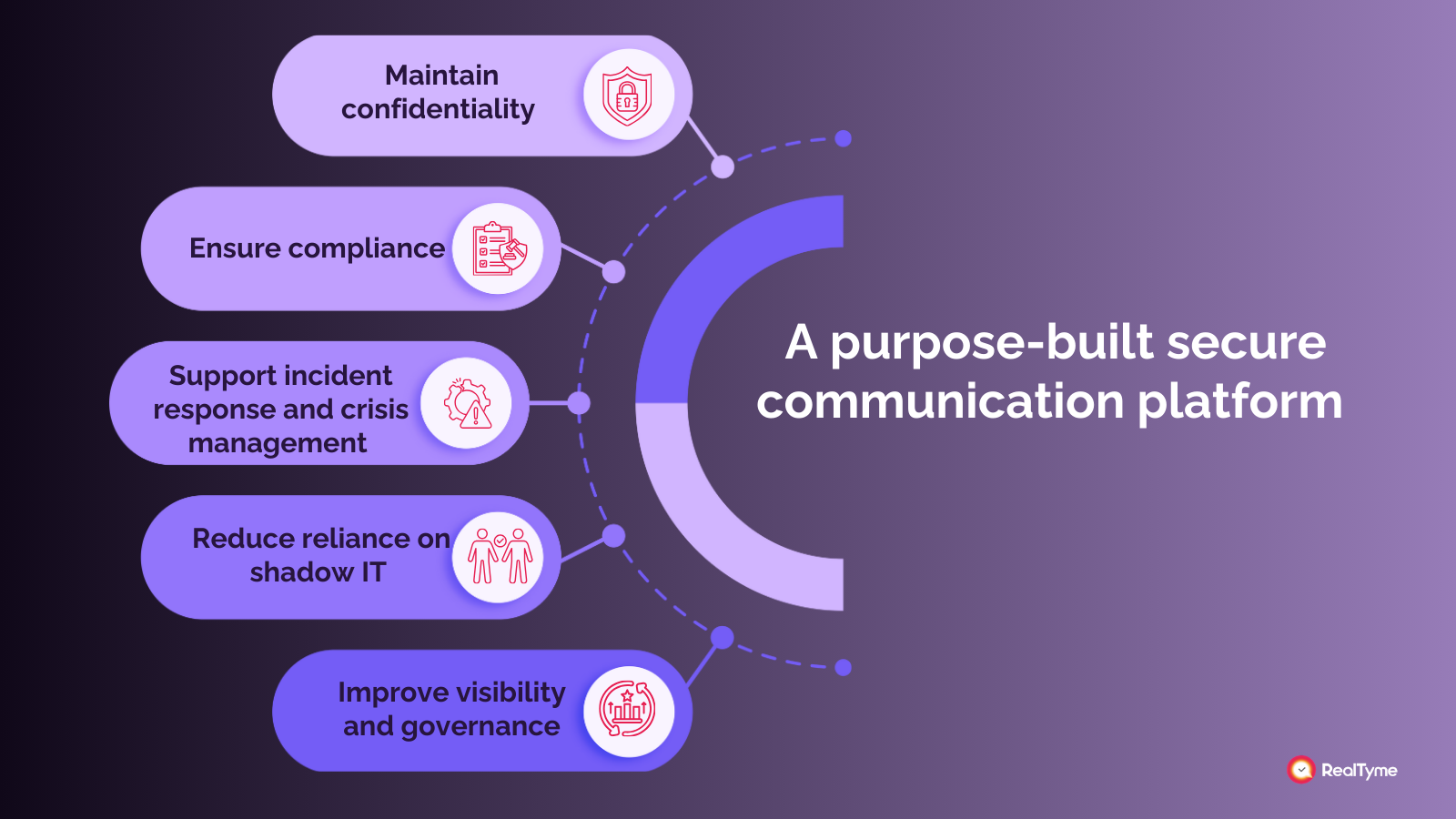
Purpose-built secure communication platforms enable organizations to:
- Maintain confidentiality during sensitive conversations, including executive discussions, crisis coordination, and operational decision-making
- Ensure compliance with data protection, privacy, and data sovereignty regulations, especially in highly regulated industries and cross-border environments
- Support incident response and crisis management through trusted, controlled communication channels that remain available when other systems are compromised
- Reduce reliance on shadow IT by providing employees with a secure, intuitive alternative that does not disrupt productivity or slow collaboration
- Improve visibility and governance, allowing organizations to enforce policies, manage access, and maintain auditability without invading user privacy
This shift reflects a broader evolution in cybersecurity thinking. Instead of relying solely on detection and remediation, organizations are embedding security directly into how people communicate every day.
In an environment where attacks increasingly target trust, identity, and human behavior, secure communication is a strategic cybersecurity capability built for the realities of 2025.
RealTyme: Built for Security-Critical Communication
RealTyme was designed for environments where privacy, trust, and compliance are non-negotiable.
Unlike consumer messaging apps or generic collaboration platforms, RealTyme is purpose-built for security-critical communication. It enables organizations to communicate securely without sacrificing speed or usability — eliminating the trade-off that consistently drove risk throughout 2025.
RealTyme is built on principles aligned with modern cybersecurity and regulatory requirements:
- Privacy by design: User content is end-to-end protected, and administrators or platform operators cannot access message content. This ensures confidentiality while maintaining organizational trust.
- Strong access and identity controls: Only verified and authorized users can communicate, reducing the risk of impersonation, social engineering, and unauthorized access.
- Centralized management and governance: Security teams can manage policies, permissions, user access, and configurations from a single management console — without compromising user privacy.
- Data sovereignty and regulatory compliance: RealTyme supports organizations operating under strict data protection and residency requirements, helping them meet regulatory obligations across jurisdictions.
- Secure-by-default architecture: Security is embedded into the platform from the ground up, rather than added as an afterthought.
Whether coordinating during a cyber incident, managing confidential executive discussions, or enabling secure collaboration across distributed teams, RealTyme supports communication when pressure is highest and margins for error are lowest.
By removing friction from secure communication, RealTyme enables organizations to move quickly without losing control.
Cybersecurity Leadership at the End of 2025
By the end of 2025, cybersecurity is firmly a business and leadership responsibility.
Boards and executive teams have learned that cyber risk directly impacts operational continuity, regulatory exposure, and organizational reputation. Communication is no longer a neutral utility, but a critical component of security posture.
Organizations that strengthened their resilience in 2025 were those that:
- Treated communication as a core part of their cybersecurity architecture
- Equipped employees with secure-by-default tools that function under pressure
- Established trusted communication channels before incidents occurred
- Aligned technology choices with privacy, compliance, and data sovereignty requirements
- Balanced security and usability to reduce shadow IT rather than accelerate it
Cybersecurity leadership today is not about slowing the business down.
It is about enabling the organization to move quickly, confidently, and securely.
What 2025 Taught Us and What Comes Next
As organizations move into 2026, the lessons of 2025 are unmistakable.
Cyber resilience is no longer defined solely by detection and response capabilities. It is defined by the ability to communicate securely when systems are degraded, trust is questioned, and decisions must be made quickly.
Secure communication is no longer the future of cybersecurity.
It is one of its most proven requirements.
RealTyme helps organizations stay secure where it matters most —
in the moments that matter most.



