How to Maintain Security in Remote Communication for Enterprises

Remote and hybrid work have become the operational backbone of modern enterprises. But the shift outside traditional office environments has dramatically widened the digital attack surface. In 2025 alone, large-scale ransomware campaigns, deepfake-driven fraud, and public-cloud outages revealed one unavoidable truth: communication systems are now mission-critical infrastructure — and they must be both secure and resilient.
Today’s organizations rely on distributed teams, cloud-based tools, and a growing mix of messaging, collaboration, and file-sharing apps. While convenient, these systems introduce vulnerabilities that adversaries actively exploit. Protecting sensitive conversations, safeguarding identities, and maintaining continuity during crises are no longer “IT concerns” — they are core components of enterprise risk management.
As communication becomes increasingly distributed, enterprises must rethink how they secure conversations, authenticate users, and maintain operational continuity during cyber incidents and outages.
So how can enterprises protect sensitive conversations, data, and operations in an increasingly remote world?
Here’s what every leader should know:
The New Reality: Remote Work Has Greatly Expanded the Enterprise Attack Surface
Remote and hybrid work have transformed the modern enterprise. What was once a temporary transition has now become a long-term operational reality. But with this shift comes a dramatic increase in exposure to cyber risks. As organizations move employees, workflows, and communication channels outside controlled office environments, the attack surface expands exponentially.
According to Gartner, 70% of enterprise communication now happens outside traditional office networks, creating new vulnerabilities that threat actors actively exploit.
1. Employees Connect Through Unsecured Networks
Remote workers frequently rely on home Wi-Fi, shared networks, and public hotspots that lack enterprise-grade protections. These environments leave communication channels vulnerable to:
- Man-in-the-middle interception
- Session hijacking
- Credential theft
- Eavesdropping on unencrypted communication
According to HP Wolf Security, nearly 30% of remote workers use unsecured public Wi-Fi for work tasks.
of remote workers use unsecured public Wi-Fi for work tasks — creating ideal conditions for attackers seeking access to sensitive business information.
2. Shadow IT and Consumer Messaging Apps Increase Risk
Remote work encourages the use of an ever-growing stack of tools: email, messaging apps, file-sharing platforms, collaboration suites, and more.
The problem? Many teams turn to convenience tools like WhatsApp, Messenger, or personal email — all of which are not designed for enterprise-grade privacy or compliance. While convenient, these apps lack:
- Strict access controls
- Zero-trust security
- Data-sovereignty protections
- Enterprise governance
- Audit trails and compliance features
- Verified user identities
Without centralized visibility and governance, security teams cannot enforce policy, maintain auditability, or ensure compliance — especially in regulated environments.
A report found that 67% of employees at Fortune 1000 companies use unapproved SaaS applications at work, contributing to widespread shadow IT and bypassing official IT tools.
3. Cloud Dependency Creates Fragility
Many organizations rely entirely on public-cloud services for communication. But cloud platforms do fail, and when they do, entire operations can come to a standstill.
The major AWS outage in October 2025 disrupted global SaaS platforms, messaging services, and enterprise applications — underscoring the risk of relying solely on third-party cloud infrastructure.
This incident demonstrated a critical lesson:
If your communication system depends entirely on a third-party cloud, your business continuity is tied to someone else’s uptime — a risk no critical organization can afford.
Single points of failure undermine resilience, especially during:
- cyberattacks
- regional outages
- natural disasters
- identity compromises
- infrastructure failures
Organizations must be able to operate even if external cloud services are down, experiencing regional outages, or under cyberattack.
4. AI-Powered Phishing, Deepfake Voices & Executive Impersonation Are Rising
Generative AI has transformed social engineering. Attackers now deploy:
- AI-written phishing campaigns
- Cloned executive voices
- Realistic video deepfakes
- Synthetic IDs
- Real-time voice impersonation during live calls
Deepfake impersonation has become one of the most effective ways for attackers to bypass technical defenses entirely by exploiting human trust.
ENISA reported a dramatic spike in deepfake-powered social-engineering attacks targeting executives in 2024–2025.
Meanwhile, Microsoft’s Digital Defense Report confirms phishing remains the #1 attack vector, now amplified by AI.
A single impersonation incident can result in fraudulent financial transfers, unauthorized system access, or catastrophic operational miscommunication. Identity verification is now a mandatory security layer.
Why This Matters: Communication Security Is Now a Business-Continuity Priority
Today, communication tools are the central nervous system of enterprise operations. If communication is:
- intercepted,
- impersonated,
- disrupted,
- or taken offline…
the entire enterprise becomes vulnerable.
When communication fails, teams cannot coordinate, leadership cannot issue instructions, and incident response stalls — multiplying the impact of any crisis.
This is why cybersecurity leaders and global agencies agree:
Secure communication is now a core pillar of business continuity and digital resilience.
NIST emphasizes secure communication channels as foundational for maintaining operational integrity during cyber incidents. As risk scales, enterprises cannot rely on consumer apps or cloud-only platforms. They need sovereign, end-to-end encrypted, identity-verified communication systems that remain operational even under attack.
Why Popular Tools Cannot Protect Enterprise Communication
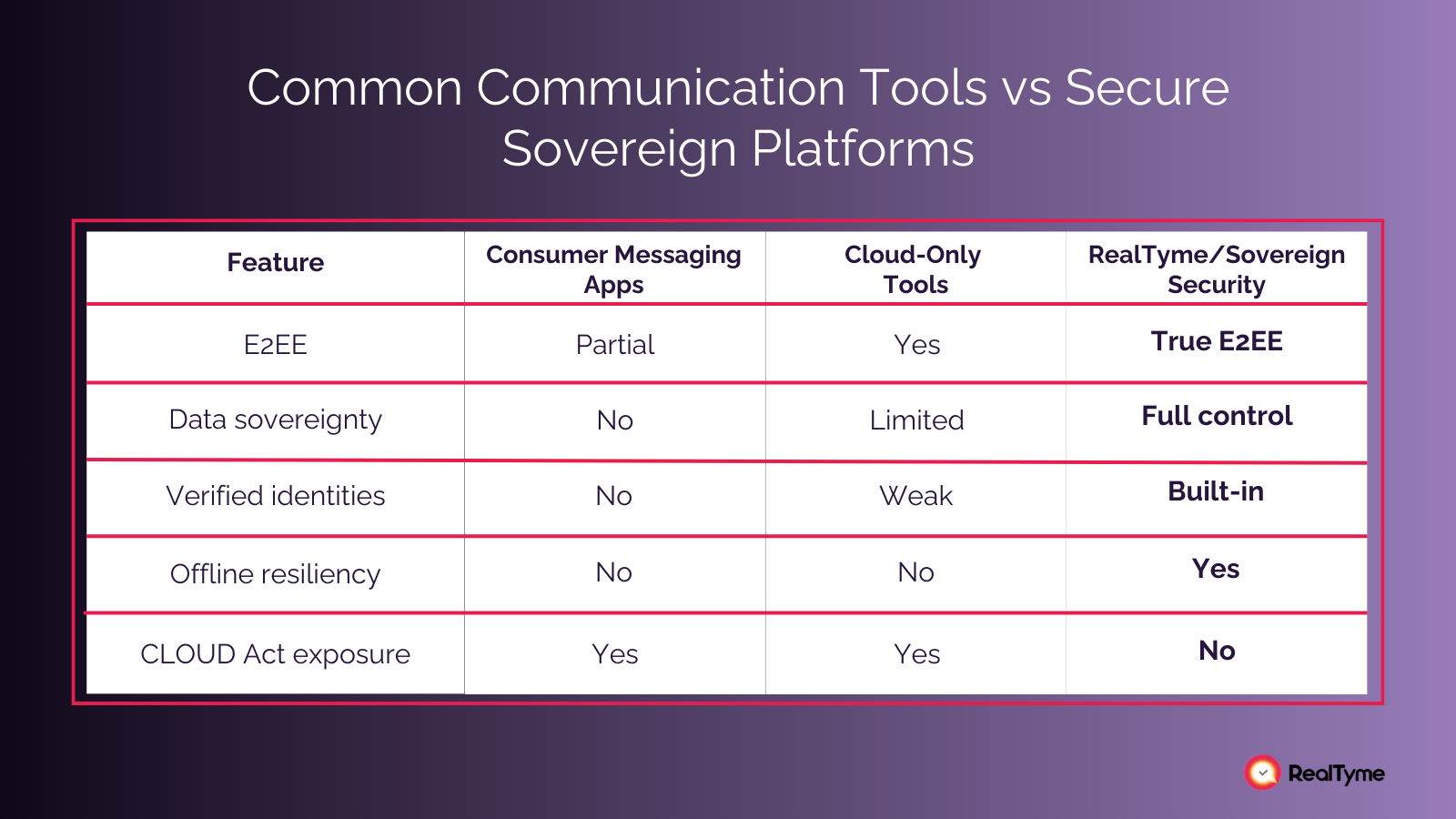
While popular communication platforms offer convenience and fast onboarding, they fall short when it comes to securing enterprise-level communication. As cyber threats evolve, the limitations of these common tools pose significant risks to business continuity, data sovereignty, and compliance.
Many widely used platforms lack essential enterprise-grade protections:
1. Partial or Weak Encryption
Many platforms use transport-level encryption rather than true end-to-end encryption (E2EE). This means service providers can still access content or keys — an unacceptable risk for regulated sectors.
2. Vendor Access to Metadata
Even if message content is encrypted, metadata (who talked to whom, when, and how frequently) often remains visible. For government, energy, finance, healthcare, or defense, metadata exposure can be as damaging as content leakage.
3. Exposure to Foreign Jurisdiction & CLOUD Act
Organizations using U.S.-based cloud services may have data disclosed to foreign authorities, regardless of server location — directly threatening digital sovereignty and regulatory compliance.
4. Weak Identity Controls
Without verified identities, deepfake and impersonation attacks easily bypass user trust, leading to financial fraud, operational disruption, and targeted exploitation.
5. Low Resilience During Outages and Crises
Cloud-native apps often fail when networks are unstable or services go offline. Ironically, this is when secure communication is needed most.
Enterprises today need far more than consumer chat apps. They require a secure, sovereign, and resilient communication platform designed to support trust, continuity, and compliance at scale.
Core Principles of Secure Remote Enterprise Communication
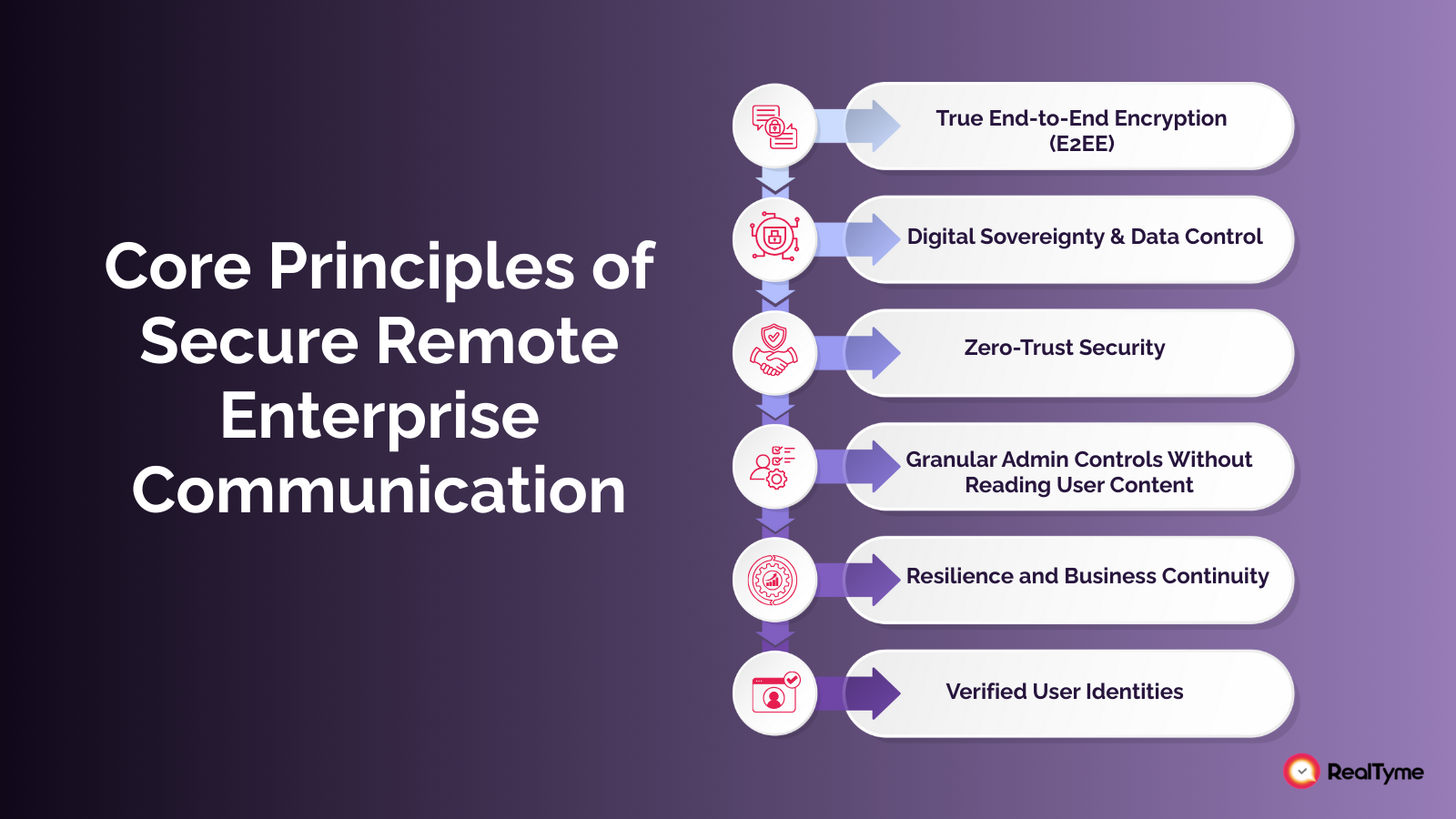
Securing remote enterprise communication requires a foundation built on sovereignty, trust, and operational resilience. These pillars are central to RealTyme’s architecture.
True End-to-End Encryption (E2EE)
Only authorized participants can access communication content. Neither vendors, admins, nor cloud providers can decrypt data — ensuring confidentiality across messaging, voice, video, and file sharing.
Digital Sovereignty & Data Control
Organizations should define:
- Where data is stored
- Who can access it
- How it is governed
Sovereign deployment models — on-premise, private cloud, hybrid — strengthen national resilience and compliance.
Zero-Trust Security
Every device, user, and session requires continuous authentication. Zero-trust eliminates implicit trust and stops lateral movement.
Granular Admin Controls Without Reading User Content
Security leaders need policy oversight without compromising privacy. RealTyme enables role-based access, compliance monitoring, and device governance — all without accessing message content.
Resilience and Business Continuity
A secure communication platform must remain operational even when networks degrade, cloud services fail, or a cyber incident is in progress. This ensures teams can coordinate during crises using infrastructure that is not dependent on a single external provider.
- networks degrade,
- services fail, or
- cyber incidents occur.
Enterprises require fallback mechanisms and local survivability — not dependence on a single cloud.
Verified, Trusted User Identities
Identity-verified communication prevents impersonation attempts, deepfake fraud, and unauthorized access — especially for executives and frontline decision-makers.
Building Resilience for the Remote-First Future
Remote work has strengthened productivity and collaboration — but it has also magnified cybersecurity, privacy, and compliance risks. Mainstream communication tools cannot deliver the sovereignty or resilience that modern enterprises demand.
To protect sensitive communication and ensure uninterrupted operations, organizations must adopt solutions engineered for secure, verified, and sovereign collaboration.
RealTyme provides this foundation.
For mission-critical environments where downtime or exposure is unacceptable, RealTyme delivers secure communication that endures outages, resists impersonation, and preserves full data sovereignty.
Talk to our experts to discover how RealTyme strengthens secure collaboration, preserves sovereignty, and ensures communication continuity across any operating condition.



